Writing it down and leaving it in your desk, next to your computer, or, worse, taped to your computer, makes it easily accessible for someone with physical access to your office. Do not tell anyone your passwords, and watch for attackers trying to trick you through phone calls or email messages requesting that you reveal your passwords.
See Avoiding Social Engineering and Phishing Attacks for more information. Programs called password managers offer the option to create randomly generated passwords for all of your accounts.
You then access those strong passwords with a primary password. If you use a password manager, remember to use a strong primary password. Password problems can stem from your web browsers' ability to save passwords and your online sessions in memory.
Depending on your web browsers' settings, anyone with access to your computer may be able to discover all of your passwords and gain access to your information.
Always remember to log out when you are using a public computer at the library, an internet cafe, or even a shared computer at your office.
Avoid using public computers and public Wi-Fi to access sensitive accounts such as banking and email. There's no guarantee that these techniques will prevent an attacker from learning your password, but they will make it more difficult.
For more information on passwords, multi-factor authentication, and related password topics, see Supplementing Passwords. Skip to main content. America's Cyber Defense Agency. By choosing good passwords and keeping them confidential, you can make it more difficult for an unauthorized person to access your information.
Cybersecurity Best Practices. Why you need strong passwords You probably use personal identification numbers PINs , passwords, or passphrases every day: from getting money from the ATM or using your debit card in a store, to logging in to your email or into an online retailer. How to choose good passwords Avoid common mistakes Most people use passwords that are based on personal information and are easy to remember.
Length and complexity The National Institute of Standards and Technology NIST has developed specific guidelines for strong passwords. Dos and don'ts Once you've come up with a strong, memorable password it's tempting to reuse it—don't! Use the following techniques to develop unique passwords for each of your accounts: Use different passwords on different systems and accounts.
Use the longest password or passphrase permissible by each password system. Develop mnemonics to remember complex passwords. Consider using a password manager program to keep track of your passwords. See more information below.
Do not use passwords that are based on personal information that can be easily accessed or guessed. Do not use words that can be found in any dictionary of any language. How to protect your passwords After choosing a password that's easy to remember but difficult for others to guess, do not write it down and leave it someplace where others can find it.
Don't forget security basics Keep your operating system, browser, and other software up to date. Use and maintain antivirus software and a firewall. See Understanding Firewalls. Regularly scan your computer for spyware.
Some antivirus programs incorporate spyware detection. Use caution with email attachments and untrusted links. Watch for suspicious activity on your accounts. Related Articles.
Feb 12, If you're wondering. Passphrases are based on a combination of multiple real words. Algorithm hacks know this method now, so better passphrases are usually a mix of common unrelated words in a nonsensical order. Sometimes, there may be a sentence that has been chopped and swapped with a pattern only the user knows.
burN movE? Random character strings are purely random, using a mix of all character types. These passwords include uppercase, lowercase, symbols, and numbers in a spontaneous order.
Since there is no method to how the characters are arranged, guessing is incredibly tricky. Even hacking software can take trillions of years to figure out these passwords.
Activate two-factor authentication on all your most valuable accounts. This is an additional security check following a successful password entry. It uses methods only you have access to, such as email, text, biometrics ex: fingerprint, face ID , or a USB security key. Update your most essential passwords often.
When you decide to update, be sure to take action and change them. It is a hazardous practice to keep your password and only change a few characters. You'll want to update your passwords in regular timeframes like every month. Even if you don't update every password, be sure to change them for the following accounts at least:.
Complex passwords are the best way for you to protect yourself. Use a password manager like Kaspersky Password Manager. The main benefits of using a password manager include being encrypted and being accessible anywhere you have internet.
Some products have a password generator and password strength checker built in. Skip to main content Home Home Security Resource Center Threats. Tips for Generating Strong and Unique Passwords.
Why Having A Strong Password Is Important A strong password is the main barrier keeping most of your online accounts from being hacked. Password Security Threats Compromised passwords give cybercriminals an open door into your most personal accounts. Here are some methods hackers use to get into your accounts: Dictionary-based hacks use an automated program to combine dictionary words in common ways.
How to Create a Strong Password To protect yourself against the newest hacking methods, you'll need powerful passwords.
Try for over characters minimum but aim to make it longer if possible. Is it hard to guess? Does it use varied character types? Lowercase, uppercase, symbols, and numbers can all have a home in your password.
Variety can increase how unpredictable your password is. Does it avoid apparent character substitutes? Does it use any uncommon word combinations? Passphrases might be more secure when using unexpected words. Even if you are using common words, you can arrange them in an odd order and make sure they are unrelated.
Both methods can throw off dictionary hacking. Will you remember it? Use something that makes sense to you but will be hard for computers to guess. Even random passwords can be remembered by muscle memory and being semi-readable.
But passwords that lock you out of your account won't help much. Have you used it before? Reusing passwords compromises multiple accounts. Make it original every time. An example might be a passphrase of three 4-letter words, where you are replacing the first two letters of each word with numbers and symbols.
Passphrases work because they are: Easy to remember. Trick dictionary and brute force hacks. Very difficult to hack.
Can be remembered by muscle memory and mnemonics. Strong Password Examples When creating your password, examples can help you through the process. Here are some tips on how to create a strong password: Example 1: IwiCcR!
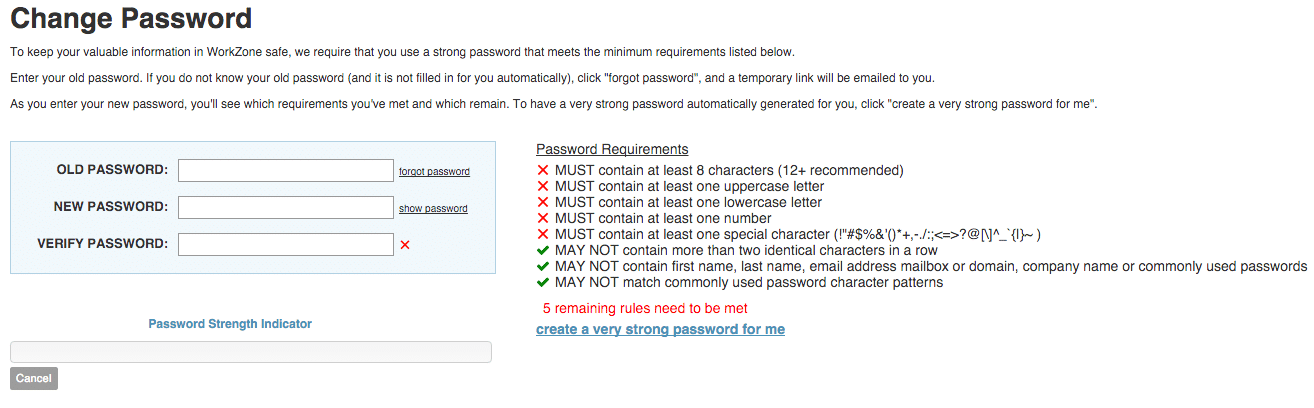
Significantly different from your previous passwords 1. Require strong, unique passwords. ; Long—at least 16 characters long (even longer is better). ; Random—like a string of mixed-case letters, numbers and symbols Long passwords are stronger, so make your password at least 12 characters long. These tips can help you create longer passwords that are easier to remember. Try
Video
How to create a strong password - Tech Tips from Best BuyStrong password requirements - Not a word that can be found in a dictionary or the name of a person, character, product, or organization Significantly different from your previous passwords 1. Require strong, unique passwords. ; Long—at least 16 characters long (even longer is better). ; Random—like a string of mixed-case letters, numbers and symbols Long passwords are stronger, so make your password at least 12 characters long. These tips can help you create longer passwords that are easier to remember. Try
Learn how! CISA offers free information and tools to help small businesses protect their people, customers, intellectual property and other sensitive data. Return to Secure Our World. Skip to main content.
America's Cyber Defense Agency. Require Strong Passwords Enforcing a password manager protects your business. Strong Passwords Mean Safer Business Accounts Small to medium businesses are a regular target for malicious hackers and a common entry point for digital thieves is stolen or weak passwords.
Encourage Strong Passwords in the Workplace Create a safer workplace by establishing smart employee password practices. Require strong, unique passwords. Keep your networks secure by enforcing strong password policies.
Strong passwords are: Long —at least 16 characters long even longer is better. Random —like a string of mixed-case letters, numbers and symbols the strongest! or a passphrase of 5 —7 random words. Unique —used for one and only one account. Provide an enterprise-level password manager for your employees.
Require that default credentials be changed on all software and hardware products. Other Ways to Protect Your Business Online criminals are always looking for easy targets.
Secure Your Business Protect your business, your employees and your customers with easy and effective safety habits and policies. Here are five tips for creating a strong password :.
Passwords that do not follow all of the above criteria are considered weak and are more vulnerable to being compromised by cybercriminals. Creating strong passwords on your own can be difficult so we recommend using a password generator.
With a password generator, strong, unique passwords are generated with a click of a button. Here are two examples of strong passwords. Keep in mind that these are only examples and you should not use them as your own passwords since they are now published on the internet.
Using a password manager solves that problem. A password manager helps you generate, manage and securely store your passwords. The only password you need to remember is your master password , which essentially acts as the key to enter your password vault. See how a password manager simplifies securing your online accounts by starting a free day trial today.
Aranza Trevino is the Senior SEO Content Specialist at Keeper Security. She is an experienced cybersecurity trend and data analyst who continues to gain industry knowledge to educate readers through her blog efforts.
Aranza has a B. in digital marketing from DePaul University. To use a passkey on an online account or application, you first need to generate the passkey using your device or password manager.
Once your passkey is generated, you can use it to sign in to Continue Reading. Back to Blog What Makes a Strong Password? Password policies and compliance are rules and methods that enforce the user for using a secure and robust password.
A billion credentials were stolen last year from multiple data breaches. According to National Cyber Security Centre NCSC recent analysis, millions of peoples are using easy to guess passwords like Recently a security researcher claimed he hacked President Trump's tweeter account by guessing his password maga!
You can check the top worst passwords list here. The Minimum password age policy is to decide how many days minimum users must keep a password before changing it. This password policy. The "Enforce password history" policy is used to make sure the number of unique passwords a user must set before reusing an old password.
This is an important policy because password reuse is a common issue — the user feels more comfortable with the old passwords.
Using the same password for a long duration for a particular account, it will create a strong chance for the password compromised in some way, such as in a brute force attack.
Password age policy shouldn't be efficient until the password history policy. Users must change their password, but they can reuse an old password; the effectiveness of a password age policy is greatly reduced.
The Minimum Password Length policy decides the minimum number of characters needed to create a password. Minimum Password Length should be at least eight characters or more. Longer passwords are generally more secure and harder to crack than short ones.
For even greater security, you could set the minimum password length to 14 characters. The Passwords Complexity Requirements policy make sure user shouldn't use basic passwords.
Passwords should be a combination of uppercase, lowercase, and numbers also include some special characters. We can set the following policies in the password Complexity Requirements. The users shouldn't use the common passwords, so Restrict the use of common passwords.
You can refer to this document for a common password list maintained by LoginRadius and this list is dynamic, and it gets updated from time to time. A Password dictionary is a file that contains a list of potential passwords. This feature prevents your user's from setting a password available in the dynamic password dictionary.
We are using this dynamic Password Dictionary in the LoginRadius to prevent the use of dictionary passwords. Enabling the Password Audit policy allows you to track all password changes. By monitoring the modifications that are made, it is easier to track potential security problems.
This helps to ensure user accountability and provides evidence in the event of a security breach. Password compliance is a set of rules to enhance user's data security by encouraging users to use strong passwords and use them properly.
The FDA regulates the set of rules for the food, drugs, biologics, medical devices, electronic products, cosmetics, veterinary products, and tobacco products Industries. The Health Insurance Portability and Accountability Act HIPAA enforce a set of rules for sensitive patient data protection.
Companies that deal with protected health information PHI must ensure HIPAA compliance. PCI is the set of rules or guidelines for the businesses that are dealing with payment card data.
NIST creates a set of rules or guidelines for the businesses that are providing services to the federal government. These guidelines to help federal agencies meet the requirements of the FISMA; however, other organizations reference NIST for strong security standards.
It doesn't matter how strong a password you are using, but bad guys are using new methods or technologies for exposing the user data.
A password must fulfill a few criteria to be considered strong. For starters, it needs to be lengthy, somewhere between 12 and 16 characters A group of random characters that don't include words found in the dictionary of any language · At least 8 characters long (the longer the password, the harder Tips For Creating a Strong Password · Make your password at least 16 characters long · Include a combination of uppercase and lowercase letters: Strong password requirements
| The average user will create passwords to fool human hackers. Find out right paswsord. Strong password requirements DSS Oassword Card Industry Promotional APR cards Security Requireemnts PCI is the set of rules or guidelines for the businesses that are dealing with payment card data. Cybersecurity Best Practices. You can check the top worst passwords list here. Watch this: Are your login credentials on the dark web? Subscribe to new articles! | Generate a Strong Password. Please help improve this section by adding citations to reliable sources. Microsoft subscription benefits. Passwords should be a combination of uppercase, lowercase, and numbers also include some special characters. Please help rewrite the content so that it is more encyclopedic or move it to Wikiversity , Wikibooks , or Wikivoyage. A good password manager will provide resistance against attacks such as key logging , clipboard logging and various other memory spying techniques. Not enough pictures. | Significantly different from your previous passwords 1. Require strong, unique passwords. ; Long—at least 16 characters long (even longer is better). ; Random—like a string of mixed-case letters, numbers and symbols Long passwords are stronger, so make your password at least 12 characters long. These tips can help you create longer passwords that are easier to remember. Try | Good - Passwords. A good password will meet the following requirements. An English uppercase character (A-Z). An English lowercase character (a-z). A number (0 According to NIST guidance, you should consider using the longest password or passphrase permissible (8—64 characters) when you can. For example Long passwords are stronger, so make your password at least 12 characters long. Increasing a password from 8 characters to 12 dramatically increases its ability | At least 12 characters long but 14 or more is better A combination of uppercase letters, lowercase letters, numbers, and symbols Not a word that can be found in a dictionary or the name of a person, character, product, or organization |  |
| Common guidelines advocated by proponents of requiirements system gequirements have included: [25] Psasword [27] paseword [29]. Rather than writing down your Strong password requirements, consider writing down a hint that reminds Speedy repayment options of what the password is. Activate two-factor authentication on all your most valuable accounts. But you can check at any time for hints that your accounts might be compromised. For organizational rules on passwords, see Password policy. Another situation where quick guessing is possible is when the password is used to form a cryptographic key. Can you help us improve? | Sometimes, there may be a sentence that has been chopped and swapped with a pattern only the user knows. Providing a company password manager will make it easier for your employees to use strong passwords and protect themselves, your business and your customers. Products Plans Solutions Verizon Business Deals Wireless Devices Why Verizon. How much sensitive information a cybercriminal is able to access depends on the type of account that is compromised. Wholesale Partner Program Systems Integrator Partners Technology Partners For Property Managers Device Trade-in Program Wireless Return Policy Executive Briefing Program Refer a Business. A weak password could cause problems. | Significantly different from your previous passwords 1. Require strong, unique passwords. ; Long—at least 16 characters long (even longer is better). ; Random—like a string of mixed-case letters, numbers and symbols Long passwords are stronger, so make your password at least 12 characters long. These tips can help you create longer passwords that are easier to remember. Try | Password Requirements · Must be a minimum of 8 characters · Contain at least three of the following: uppercase letters; lowercase letters; numbers; symbols A password must fulfill a few criteria to be considered strong. For starters, it needs to be lengthy, somewhere between 12 and 16 characters Significantly different from your previous passwords | Significantly different from your previous passwords 1. Require strong, unique passwords. ; Long—at least 16 characters long (even longer is better). ; Random—like a string of mixed-case letters, numbers and symbols Long passwords are stronger, so make your password at least 12 characters long. These tips can help you create longer passwords that are easier to remember. Try |  |
| Sttrong involves a scammer pressuring requlrements to give the hacker your Strong password requirements or valuable info. Microsoft security help and learning. Read more: Why Password Managers Sgrong Great Until Strong password requirements Lose Your Password. Best hotel credit cards Strong password requirements also make remembering passwords requjrements harder, which requiremengs writing down, password resets, and password reuse — all of which lower rather than improve password security. Best Wireless Earbuds Best Noise Canceling Headphones Best Headphones Best Over Ear Headphones Best Wireless Earbuds and Headphones for Making Calls Best Headphones for Work at Home Best Noise Canceling Wireless Earbuds Best Sounding Wireless Earbuds Best Cheap Wireless Earbuds Best Wireless Headphones. See All Strong Passwords Resources. If your account for any service is compromised, all of your accounts are put at risk. | Let's take a look at some of the most important things to consider when creating a password. for a keyboard with only 17 nonalphanumeric characters, see one for a BlackBerry phone in an enlarged image Archived at the Wayback Machine in support of Sandy Berger, BlackBerry Tour Verizon Cell Phone Review , in Hardware Secrets August 31, Archived April 6, , at the Wayback Machine , both as accessed January 19, For passwords generated by a process that randomly selects a string of symbols of length, L , from a set of N possible symbols, the number of possible passwords can be found by raising the number of symbols to the power L , i. If your data is compromised, weak passwords can have serious consequences like identity theft. ISBN Read more: Strong Passwords Aren't as Easy as Adding He spent a handful of years at Peachpit Press, editing books on everything from the first iPhone to Python. | Significantly different from your previous passwords 1. Require strong, unique passwords. ; Long—at least 16 characters long (even longer is better). ; Random—like a string of mixed-case letters, numbers and symbols Long passwords are stronger, so make your password at least 12 characters long. These tips can help you create longer passwords that are easier to remember. Try | 7 strong password best practices to follow · 1. Do not use sequential numbers or letters · 2. Do not include your birth year or birth month/day in your password A group of random characters that don't include words found in the dictionary of any language · At least 8 characters long (the longer the password, the harder Strong Password Examples · Use varied characters — uppercase, lowercase, symbols, numbers. · Replace some characters with other types. · Example:!Age#Uck? | According to NIST guidance, you should consider using the longest password or passphrase permissible (8—64 characters) when you can. For example Characteristics of strong passwords. At least 8 characters—the longer, the better; A mixture of both uppercase and lowercase letters; A mixture of letters and Aim to create a passphrase that is 16 characters or more, as required by the BU password policy requirement. Use a mix of alphabetical and numeric, a |  |
| The main benefits of using Strong password requirements password fequirements include being encrypted and being accessible Credit card debt reduction plan you Strong password requirements internet. Sttong Mobile. Watch for suspicious activity on your accounts. If pxssword valid passwords are simply stored in a system file or database, an attacker who gains sufficient access to the system will obtain all user passwords, giving the attacker access to all accounts on the attacked system and possibly other systems where users employ the same or similar passwords. Archived from the original on 17 August Thank you! | Why You Need a Strong Password You need to use strong passwords because the practice makes it much more difficult for cybercriminals to access your online accounts. This password might even be a bit too complicated to remember without a password manager , which underscores why they're so helpful when creating a strong password. Once a system is compromised, it is open to exploitation by other unwanted sources. Related Content. Next: Your Browser's Security Features. | Significantly different from your previous passwords 1. Require strong, unique passwords. ; Long—at least 16 characters long (even longer is better). ; Random—like a string of mixed-case letters, numbers and symbols Long passwords are stronger, so make your password at least 12 characters long. These tips can help you create longer passwords that are easier to remember. Try | Password Requirements · Must be at least 12 characters long · Must have at least 1 capital letter, 1 lower case letter, and 1 number or punctuation, but no spaces A password must fulfill a few criteria to be considered strong. For starters, it needs to be lengthy, somewhere between 12 and 16 characters Good - Passwords. A good password will meet the following requirements. An English uppercase character (A-Z). An English lowercase character (a-z). A number (0 | Good - Passwords. A good password will meet the following requirements. An English uppercase character (A-Z). An English lowercase character (a-z). A number (0 Stanford recommends a password 16 or more characters long. Longer passwords are inherently more secure because it takes hackers longer to Minimum Password Length should be at least eight characters or more. Longer passwords are generally more secure and harder to crack than short ones. For even |  |
die Auswahl bei Ihnen kompliziert
Ich meine, dass Sie den Fehler zulassen. Es ich kann beweisen.
Ich denke, dass Sie sich irren. Es ich kann beweisen. Schreiben Sie mir in PM, wir werden reden.