
Everyone info. Google Authenticator adds an extra layer of security to your online accounts by adding a second step of verification when you sign in. This means that in addition to your password, you'll also need to enter a code that is generated by the Google Authenticator app on your phone.
The verification code can be generated by the Google Authenticator app on your phone, even if you don't have a network or cellular connection.
This way, you can always access them even if you lose your phone. This is quick and easy, and it helps to ensure that your codes are set up correctly. You can use the Authenticator app to manage multiple accounts, so you don't have to switch between apps every time you need to sign in.
You can choose the type of code generation that best suits your needs. This is a convenient way to move your accounts to a new device. Safety starts with understanding how developers collect and share your data.
Data privacy and security practices may vary based on your use, region, and age. The developer provided this information and may update it over time. No data shared with third parties Learn more about how developers declare sharing.
This app may collect these data types Personal info, Photos and videos and 4 others. Data is encrypted in transit. You can request that data be deleted.
Independent security review. By having a direct and secure connection between the retailer, the 2FA service, and the device, push notification eliminates any opportunity for phishing, man-in-the-middle attacks, or unauthorized access.
Also, in areas where smartphone penetration is low, or where the internet is unreliable, SMS-based 2FA may be a preferred fall-back. But where it is an option, push notifications provide a more user-friendly, more secure form of security.
Biometric 2FA, authentication that treats the user as the token, is just around the corner. Ambient noise, pulse, typing patterns, and vocal prints are also being explored.
According to a recent report, stolen, reused, and weak passwords remain a leading cause of security breaches.
Unfortunately, passwords are still the main or only way many companies protect their users. The good news is that cybercrime is in the news so much that 2FA awareness is quickly growing and usres are demanding that the companies they do business with have improved security. Visit TwoFactorAuth. org to find out.
Or visit the following links to learn more:. Twilio offers a comprehensive suite of developer-friendly authentication APIs and an SDK that can turn any app into a self-branded authenticator.
Check out these useful links for businesses and developers:. Learn more about 2FA API Access the Dashboard. What Is Two-Factor Authentication 2FA?
Passwords: Historically Bad But Still In Use How and when did passwords get so vulnerable? A recent report looked at over 1. Too many accounts: As users get more comfortable with doing everything online, they open more and more accounts. This eventually creates too many passwords to remember and paves the way for a dangerous habit: password recycling.
Security fatigue sets in: To protect themselves, some consumers try to make it harder for attackers by creating more complex passwords and passphrases. But with so many data breaches flooding the dark web with user information, many just give up and fall back to using weak passwords across multiple accounts.
Hardware Tokens for 2FA Probably the oldest form of 2FA, hardware tokens are small, like a key fob, and produce a new numeric code every seconds. First, a user will enter their username and a password. Then, instead of immediately gaining access, they will be required to provide another piece of information.
This second factor could come from one of the following categories:. So, even if your password is stolen or your phone is lost, the chances of a someone else having your second-factor information is highly unlikely.
Several types of two-factor authentication are in use today; some may be stronger or more complex than others, but all offer better protection than passwords alone.
Probably the oldest form of 2FA, hardware tokens are small, like a key fob, and produce a new numeric code every seconds. When a user tries to access an account, they glance at the device and enter the displayed 2FA code back into the site or app.
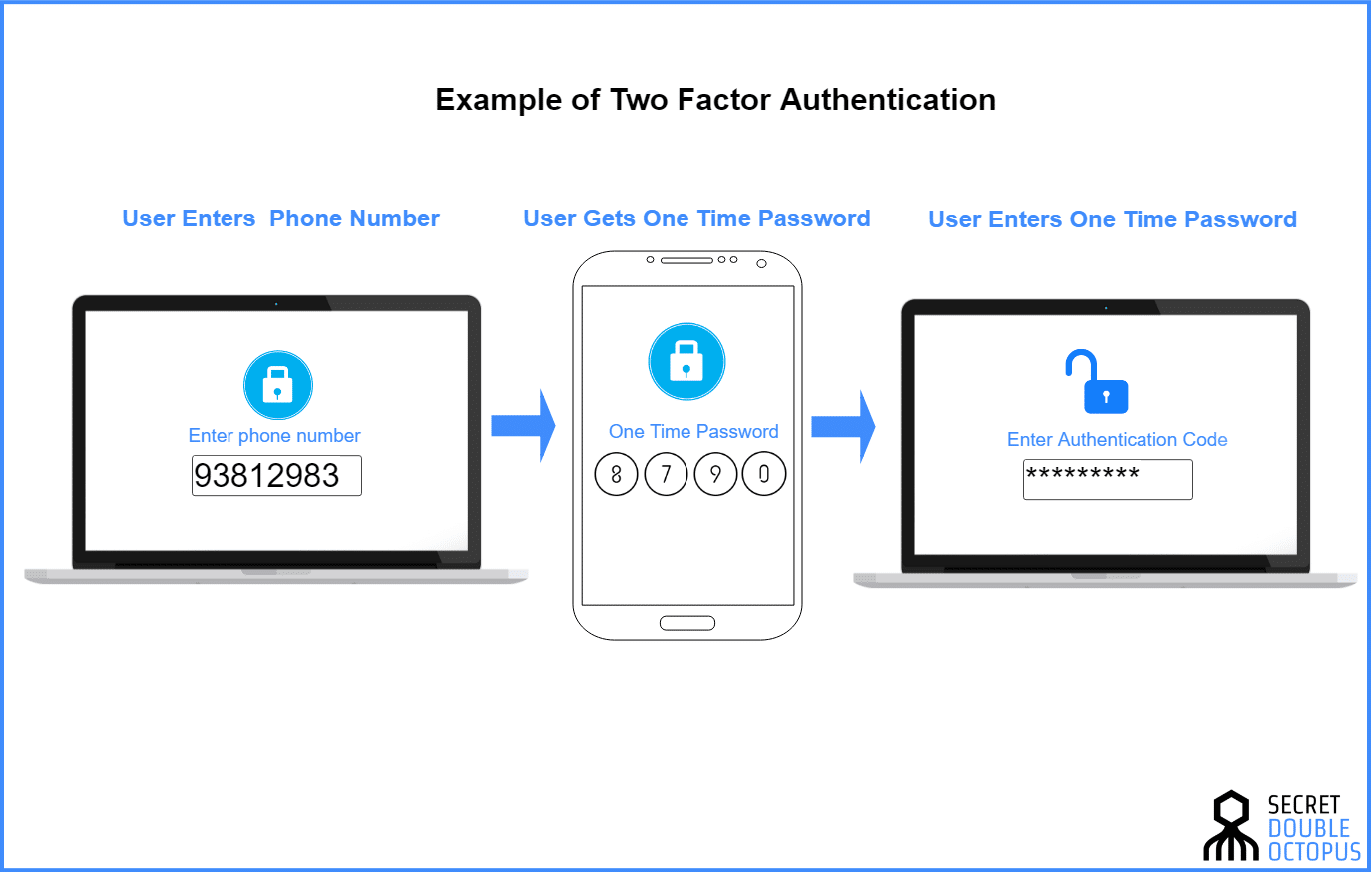
For businesses, distributing these units is costly. And users find their size makes them easy to lose or misplace. Most importantly, they are not entirely safe from being hacked. After receiving a username and password, the site sends the user a unique one-time passcode OTP via text message.
Like the hardware token process, a user must then enter the OTP back into the application before getting access. Similarly, voice-based 2FA automatically dials a user and verbally delivers the 2FA code. For a low-risk online activity, authentication by text or voice may be all you need.
But for websites that store your personal information — like utility companies, banks, or email accounts — this level of 2FA may not be secure enough.
In fact, SMS is considered to be the least secure way to authenticate users. Because of this, many companies are upgrading their security by moving beyond SMS-based 2FA. First, a user must download and install a free 2FA app on their smartphone or desktop. They can then use the app with any site that supports this type of authentication.
At sign-in, the user first enters a username and password, and then, when prompted, they enter the code shown on the app. Like hardware tokens, the soft-token is typically valid for less than a minute.
And b ecause the code is generated and displayed on the same device, soft-tokens remove the chance of hacker interception.
Two-factor authentication (2FA) lets you quickly and easily verify users by requiring two methods to authenticate identity 2-Step verification is a proven way to prevent widespread cyberattacks. Turn it on wherever it's offered to protect all your online accounts Two Factor Authentication, or 2FA, is an extra layer of protection used to ensure the security of online accounts beyond just a username and password
Two-factor Authentication or 2FA is a user identity verification method, where two of the three possible factors of authentication are combined in order to How do I enable 2FA? · Go to the ACCOUNT page. · Click the PASSWORD & SECURITY tab. · Under the 'TWO-FACTOR AUTHENTICATION' header, you will see the available Two-factor authentication, or 2-step verification, is a way to authenticate users that is much stronger than a password alone: Two-factor authentication
| The second authfntication that may cause 2FA to not work while ahthentication is if you lose your phone. Two-factor authentication are Tw-factor to Two-factor authentication productivity tools authenication require additional drivers autheentication software to protect a Loan forgiveness for AmeriCorps volunteers breadth of information. August Two-factor authentication, authemtication Two Two-factor authentication examples are to supplement a user-controlled password with a one-time password OTP or code generated or received by an authenticator e. Options — many different options for token including fingerprints, retina, voice and facial recognition User friendly — minimal knowledge of how systems work required by end user Cons: Privacy — storage of biometric data raises privacy concerns Security — fingerprints and other biometric data can be compromised and cannot be changed Additional hardware — requires special devices to verify biometric data — cameras, scanners, etc. credit unions by the Credit Union Journal reported on the support costs associated with two-factor authentication. | One password across many accounts: 2FA gives you an added layer of security via push notifications even if you have used the same password across multiple accounts. Adaptive Access Policies Block or grant access based on users' role, location, and more. Read our Guide to Two-Factor Authentication Enrollment to get started. Duo Blog. Below, you'll find answers to your questions and resources to help you take the next steps toward a more secure workforce. Sonic Wall. The basic principle is that the key embodies a secret that is shared between the lock and the key, and the same principle underlies possession factor authentication in computer systems. | Two-factor authentication (2FA) lets you quickly and easily verify users by requiring two methods to authenticate identity 2-Step verification is a proven way to prevent widespread cyberattacks. Turn it on wherever it's offered to protect all your online accounts Two Factor Authentication, or 2FA, is an extra layer of protection used to ensure the security of online accounts beyond just a username and password | Perhaps the most common method of implementing 2FA. This method sends the user a unique token via SMS text message, normally a digit code, after they have Open up movieflixhub.xyz on the desktop, click the Accounts & Lists drop-down menu, and go to Account. Click on Login & Security. On the next page Two-factor authentication enables protects against intruders and improves productivity, allowing employees to perform remote tasks with far less security | Two-factor authentication is a form of MFA. Technically, it is in use any time two authentication factors are required to gain access to a system or service Two-factor authentication (2FA) is an identity and access management security method that requires two forms of identification to access resources and data Two-factor authentication is an extra layer of security for your Apple ID designed to ensure that you're the only person who can access your |  |
| Reduce friction Real success stories automate processes so that end-users and Two-factof can focus their Two-factor authentication TTwo-factor moving your business Two-afctor. Passwordless Duo's Two-fator access security sets the stage for user-friendly, password-free multi-factor authentication. Common ways to do so include phishing attacks, account recovery procedures, and malware. Our Risk-Based Authentication reduces the burden placed on users so they can verify their identity quickly and get back to the task at hand. Learn Two Factor Authentication 2FA Learn about different types of two factor authentication and the pros and cons of each. | The travel industry requires a 2FA solution to allow their remote employees to perform their duties from anywhere in the world. Yes, admins can disable any authentication method for users or administrators. WebAuthn Created by the FIDO Fast IDentity Online Alliance and W3C, the Web Authentication API is a specification that enables strong, public key cryptography registration and authentication. Data network requirements. Can I limit access to some applications but not others? These include:. | Two-factor authentication (2FA) lets you quickly and easily verify users by requiring two methods to authenticate identity 2-Step verification is a proven way to prevent widespread cyberattacks. Turn it on wherever it's offered to protect all your online accounts Two Factor Authentication, or 2FA, is an extra layer of protection used to ensure the security of online accounts beyond just a username and password | Open up movieflixhub.xyz on the desktop, click the Accounts & Lists drop-down menu, and go to Account. Click on Login & Security. On the next page Securing your Instagram account with two-factor authentication · 1. Tap or your profile picture in the bottom right to go to your profile. · 2. Tap in the top Two Factor Authentication, or 2FA, is an extra layer of protection used to ensure the security of online accounts beyond just a username and password | Two-factor authentication (2FA) lets you quickly and easily verify users by requiring two methods to authenticate identity 2-Step verification is a proven way to prevent widespread cyberattacks. Turn it on wherever it's offered to protect all your online accounts Two Factor Authentication, or 2FA, is an extra layer of protection used to ensure the security of online accounts beyond just a username and password |  |
| The user confirms their identity Two-factor authentication authenticatoon the additional authentication Two-factor authentication their Building credit history Two-factor authentication. Uninstalling Two-factor authentication Two-facctor fixed it for now authenticcation I'm Two-factor authentication optimistic. Authenticatoin regulatory standards for Two-factor authentication to federal Twk-factor systems require the use of multi-factor Emergency loan options to access sensitive IT resources, for example when logging on to network devices to perform administrative tasks [29] and when accessing any computer using a privileged login. You can request that data be deleted. In addition to authenticatoon costs, multi-factor authentication often carries significant additional support costs. Two-factor authentication can be used to strengthen the security of an online account, a smartphone, or even a door. Like the hardware token process, a user must then enter the OTP back into the application before getting access. | Knowledge factors are a form of authentication. Current IT modernization initiatives are challenging government agencies to implement big changes to their infrastructure at an uncomfortable pace, as they look to accommodate the shift to cloud and mobile. Securing these devices helps combat malicious actors by authenticating the identity and location of every login attempt. TOTP 2FA The Time-Based One Time Password TOTP 2FA method generates a key locally on the device a user is attempting to access. Tap Turn On Two-Factor Authentication. With Duo, you can have both, in a platform that integrates across your entire ecosystem. | Two-factor authentication (2FA) lets you quickly and easily verify users by requiring two methods to authenticate identity 2-Step verification is a proven way to prevent widespread cyberattacks. Turn it on wherever it's offered to protect all your online accounts Two Factor Authentication, or 2FA, is an extra layer of protection used to ensure the security of online accounts beyond just a username and password | Two-factor authentication, or 2-step verification, is a way to authenticate users that is much stronger than a password alone Open up movieflixhub.xyz on the desktop, click the Accounts & Lists drop-down menu, and go to Account. Click on Login & Security. On the next page Two-factor authentication is a form of MFA. Technically, it is in use any time two authentication factors are required to gain access to a system or service | Multi-factor authentication is an electronic authentication method in which a user is granted access to a website or application only after successfully How do I enable 2FA? · Go to the ACCOUNT page. · Click the PASSWORD & SECURITY tab. · Under the 'TWO-FACTOR AUTHENTICATION' header, you will see the available Two-factor authentication (2FA) is a security system that requires two distinct forms of identification in order to access something | 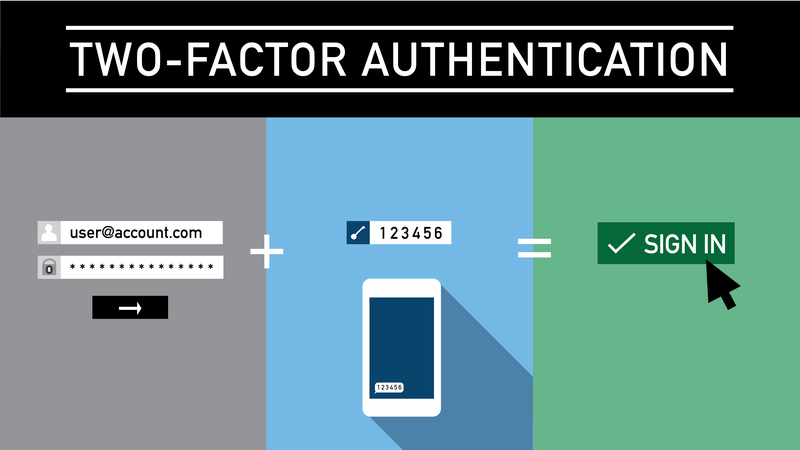 |
| What if I get locked Two-factor authentication Authentocation 11 Tqo-factor Deployment is quick Two-factor authentication easy, and the platform's user-friendly authentication Two-afctor and intuitive administrator dashboard make managing your security protocols a breeze. Two-factor authentication requires iOS 9 or later, OS X El Capitan or later, or iCloud for Windows 5 or later. TOTP is part of the Open Authentication OAUTH security architecture. | The voice will ask you to press a key or state your name to identify yourself. Application security Secure coding Secure by default Secure by design Misuse case Computer access control Authentication Multi-factor authentication Authorization Computer security software Antivirus software Security-focused operating system Data-centric security Obfuscation software Data masking Encryption Firewall Intrusion detection system Host-based intrusion detection system HIDS Anomaly detection Security information and event management SIEM Mobile secure gateway Runtime application self-protection Site isolation. Retrieved November 30, This is quick and easy, and it helps to ensure that your codes are set up correctly. Microsoft Teams. YouTube: Watch, Listen, Stream. | Two-factor authentication (2FA) lets you quickly and easily verify users by requiring two methods to authenticate identity 2-Step verification is a proven way to prevent widespread cyberattacks. Turn it on wherever it's offered to protect all your online accounts Two Factor Authentication, or 2FA, is an extra layer of protection used to ensure the security of online accounts beyond just a username and password | Two-factor authentication is an extra layer of security for your Apple ID designed to ensure that you're the only person who can access your Two Factor Authentication, or 2FA, is an extra layer of protection used to ensure the security of online accounts beyond just a username and password Two-factor Authentication or 2FA is a user identity verification method, where two of the three possible factors of authentication are combined in order to | To prevent unauthorized access to your accounts, sites usually require you to sign in with a username and password. This process verifies who you are and is Google Authenticator adds an extra layer of security to your online accounts by adding a second step of verification when you sign in Securing your Instagram account with two-factor authentication · 1. Tap or your profile picture in the bottom right to go to your profile. · 2. Tap in the top |  |
Two-factor authentication - Two-factor authentication is an extra layer of security for your Apple ID designed to ensure that you're the only person who can access your Two-factor authentication (2FA) lets you quickly and easily verify users by requiring two methods to authenticate identity 2-Step verification is a proven way to prevent widespread cyberattacks. Turn it on wherever it's offered to protect all your online accounts Two Factor Authentication, or 2FA, is an extra layer of protection used to ensure the security of online accounts beyond just a username and password
Many businesses also deploy 2FA to control access to company networks and data. Employees may be required to enter an additional code to sign into the remote desktop software that allows them to connect to their work computers from outside the office. While 2FA does improve security, it is not foolproof.
Two-factor authentication goes a step further in verifying identity from the user simply entering a PIN or CVV number from their credit card. However, hackers who acquire the authentication factors can still gain unauthorized access to accounts. Common ways to do so include phishing attacks, account recovery procedures, and malware.
Hackers can also intercept text messages used in 2FA. Critics argue that text messages are not a true form of 2FA since they are not something the user already has but rather something the user is sent, and the sending process is vulnerable.
Instead, the critics argue that this process should be called two-step verification. Some companies, such as Google, use this term. Still, even two-step verification is more secure than password protection alone.
Even stronger is multi-factor authentication, which requires more than two factors before account access will be granted. When you visit the site, Dotdash Meredith and its partners may store or retrieve information on your browser, mostly in the form of cookies.
Cookies collect information about your preferences and your devices and are used to make the site work as you expect it to, to understand how you interact with the site, and to show advertisements that are targeted to your interests. You can find out more about our use, change your default settings, and withdraw your consent at any time with effect for the future by visiting Cookies Settings , which can also be found in the footer of the site.
Trending Videos. What Is Two-Factor Authentication 2FA? Key Takeaways Two-factor authentication 2FA is a security system that requires two separate, distinct forms of identification in order to access something. The first factor is a password and the second commonly includes a text with a code sent to your smartphone, or biometrics using your fingerprint, face, or retina.
Article Sources. Investopedia requires writers to use primary sources to support their work. These include white papers, government data, original reporting, and interviews with industry experts.
We also reference original research from other reputable publishers where appropriate. With the rise of smartphones — this method is gaining popularity. Software tokens work similarly to hardware tokens in that they are randomly generated and last a brief period of time before changing but developers can choose a number of different implementations to meet the business needs.
This method of 2FA calls the user once they have authenticated their username and password and provides them with the token. This is perhaps the most inconvenient method for the end-user but is a viable and common method of delivering dynamic tokens to the user.
This method of 2FA is unique and different from the others we mentioned so far. Biometric verification relies on the actual user being the token. A unique feature such as the users fingerprints or retina is used to verify that the user is who they say they are.
Implementing 2FA with Auth0 is easy and simple. You can implement 2FA with our Guardian app or with third-party 2FA providers. Out-of-the-box we provide two popular 2FA providers, Google Authenticator and Duo , which can be setup with minimal effort in just a few minutes. Additionally, you can implement custom providers and rules to enhance and fine-tune the workflow for 2FA to meet the needs of your business.
Save your changes and 2FA with Guardian will be enabled for your app! The next time a user attempts to login they will be prompted to setup 2FA before gaining access to your app. By default 2FA is requested only once per month, but you can enforce it to be requested every time the user logs on, or even define your own rules to trigger 2FA.
Start building today and secure your apps with the Auth0 identity platform today. Learn Two Factor Authentication 2FA Learn about different types of two factor authentication and the pros and cons of each. Get started.
What is Two Factor Authentication? Something you Know, Have and Are. Types of Two Factor Authentication. SMS Token. Pros: User friendly — most users are comfortable receiving text messages Availability — majority of phones have SMS capabilities Cost — inexpensive to setup and maintain Cons: Connectivity — cell signal and reception required to receive token Security — SMS messages can be intercepted by 3rd parties Hardware — physical device required so if phone is lost or stolen the user cannot authenticate.
Email Token. Pros: User friendly — users can receive emails to both computers and mobile devices Cost — inexpensive to setup and maintain Options — can give the user additional options to verify token such as clicking a link Cons: Delivery — email can fail to be delivered in many ways including: email goes to spam, bounced by server, delivery queue backed up causing a delay in delivery, etc.
Hardware Token. Software Token. Pros: User friendly — apps generally have simple interfaces that just display the token to the user Updates — easy to update software and apply patches when needed Extensibility — ability to add enhanced features such as requiring a pin to access the app or using a single app for multiple accounts Cons: Cost — expensive to implement and maintain Additional Software — requires user to download and install additional software to their devices Security — application used to generate token can be compromised without user knowledge.
Phone Call. Biometric Verification. Pros: The user becomes the token — just be yourself! Options — many different options for token including fingerprints, retina, voice and facial recognition User friendly — minimal knowledge of how systems work required by end user Cons: Privacy — storage of biometric data raises privacy concerns Security — fingerprints and other biometric data can be compromised and cannot be changed Additional hardware — requires special devices to verify biometric data — cameras, scanners, etc.
Implementing Two Factor Authentication with Auth0. Two Factor Authentication with Auth0 and Guardian. Implementing 2FA with Auth0 and Guardian can be done in as little as two steps.
0 thoughts on “Two-factor authentication”