
Online criminals are always looking for easy targets. Take the following steps to make it harder for malicious actors to access your data or trick an employee into allowing access to your systems. Protect your business, your employees and your customers with easy and effective safety habits and policies.
This is one of the easiest ways to protect your business from criminals who might otherwise access your accounts by guessing or automating hacking programs. Using more than a password to access an account—such as a texted code, authenticator app, fingerprint or access card—makes an account safer than a password alone!
Flaws give criminals an opening. Programmers publish patches, but you must install them to get their protection. Clicking a phishing link can lead to downloading ransomware which can threaten your business.
Get resources to tackle ransomware more effectively. CISA offers free information and tools to help small businesses protect their people, customers, intellectual property and other sensitive data. Return to Secure Our World. Skip to main content. America's Cyber Defense Agency.
Teach Employees to Avoid Phishing Equip your staff to recognize and report phishing scams that could threaten your business. Protect Your Business with Phishing Training Most successful online attacks begin when someone clicks and downloads a malicious attachment from an email, direct message or social media post.
Follow These Steps to Avoid Phishing Scams 1. Identify available training resources and train employees how to spot phishing. Alert employees to the risks. Develop a culture of awareness. CISA has many resources to get your team started with online safety! Other Ways to Protect Your Business Online criminals are always looking for easy targets.
Secure Your Business Protect your business, your employees and your customers with easy and effective safety habits and policies. Require Strong Passwords This is one of the easiest ways to protect your business from criminals who might otherwise access your accounts by guessing or automating hacking programs.
Require Multifactor Authentication Using more than a password to access an account—such as a texted code, authenticator app, fingerprint or access card—makes an account safer than a password alone!
Update Business Software Flaws give criminals an opening. Related Content. Keep your eyes peeled for news about new phishing scams. By finding out about them as early as possible, you will be at much lower risk of getting snared by one.
For IT administrators, ongoing security awareness training and simulated phishing for all users is highly recommended in keeping security top of mind throughout the organization. Think Before You Click! Hover over links that you are unsure of before clicking on them. Do they lead where they are supposed to lead?
A phishing email may claim to be from a legitimate company and when you click the link to the website, it may look exactly like the real website. The email may ask you to fill in the information but the email may not contain your name. When in doubt, go directly to the source rather than clicking a potentially dangerous link.
Install an Anti-Phishing Toolbar — Most popular Internet browsers can be customized with anti-phishing toolbars. Such toolbars run quick checks on the sites that you are visiting and compare them to lists of known phishing sites. If you stumble upon a malicious site, the toolbar will alert you about it.
This is just one more layer of protection against phishing scams, and it is completely free. If you get a message stating a certain website may contain malicious files, do not open the website. Never download files from suspicious emails or websites.
Even search engines may show certain links which may lead users to a phishing webpage which offers low cost products.
If the user makes purchases at such a website, the credit card details will be accessed by cybercriminals. Get into the habit of changing your passwords regularly too. To prevent bank phishing and credit card phishing scams, you should personally check your statements regularly.
Get monthly statements for your financial accounts and check each and every entry carefully to ensure no fraudulent transactions have been made without your knowledge. Keep Your Browser Up to Date — Security patches are released for popular browsers all the time.
They are released in response to the security loopholes that phishers and other hackers inevitably discover and exploit. If you typically ignore messages about updating your browsers, stop.
The minute an update is available, download and install it. Use Firewalls — High-quality firewalls act as buffers between you, your computer and outside intruders. You should use two different kinds: a desktop firewall and a network firewall.
The first option is a type of software, and the second option is a type of hardware. When used together, they drastically reduce the odds of hackers and phishers infiltrating your computer or your network. Be Wary of Pop-Ups — Pop-up windows often masquerade as legitimate components of a website.
All too often, though, they are phishing attempts. Many popular browsers allow you to block pop-ups; you can allow them on a case-by-case basis. Never Give Out Personal Information — As a general rule, you should never share personal or financially sensitive information over the Internet.
This rule spans all the way back to the days of America Online, when users had to be warned constantly due to the success of early phishing scams.
Use strong passwords & enable two-factor authentication Don't ignore update messages Exercise caution when opening emails or clicking on links
Regularly changing the passwords to online accounts is an effective phishing protection measure. Doing so will prevent many attacks, including bank and credit Missing How to Recognize and Avoid Phishing Scams · 1. Protect your computer by using security software. · 2. Protect your cell phone by setting software to update: Anti-phishing measures
| See the Anti-phishing measures threats that are Anti-phishing measures Anti-pgishing your Anti-phisshing Email Gateway SEG. Supercharge your Security Awareness Training so employees can easily spot and report actual threats. When they target companies, they use more specific methods:. Average rating 4. Functional Functional. | Instead, open your browser window and type the address directly into the URL field so you can make sure the site is real. Effectively learning how to prevent phishing will require a similar commitment from your side. You'll learn how to:. Phishing mainly jeopardises the security of confidential data of a company, as well as its finances:. Contact us. | Use strong passwords & enable two-factor authentication Don't ignore update messages Exercise caution when opening emails or clicking on links | The term 'anti-phishing' thus refers to measures taken to prevent these phishing attacks. Understanding Phishing. Phishing is a form of cyber attack that 1. Keep Informed About Phishing Techniques · 2. Think Before You Click! · 3. Install an Anti-Phishing Toolbar · 4. Verify a Site's Security – · 4. Verify a Site's Four layers of mitigation · Layer 1: Make it difficult for attackers to reach your users · Don't let your email addresses be a resource for attackers · Reduce the | Know what a phishing scam looks like Get free anti-phishing add-ons Conduct security awareness training | 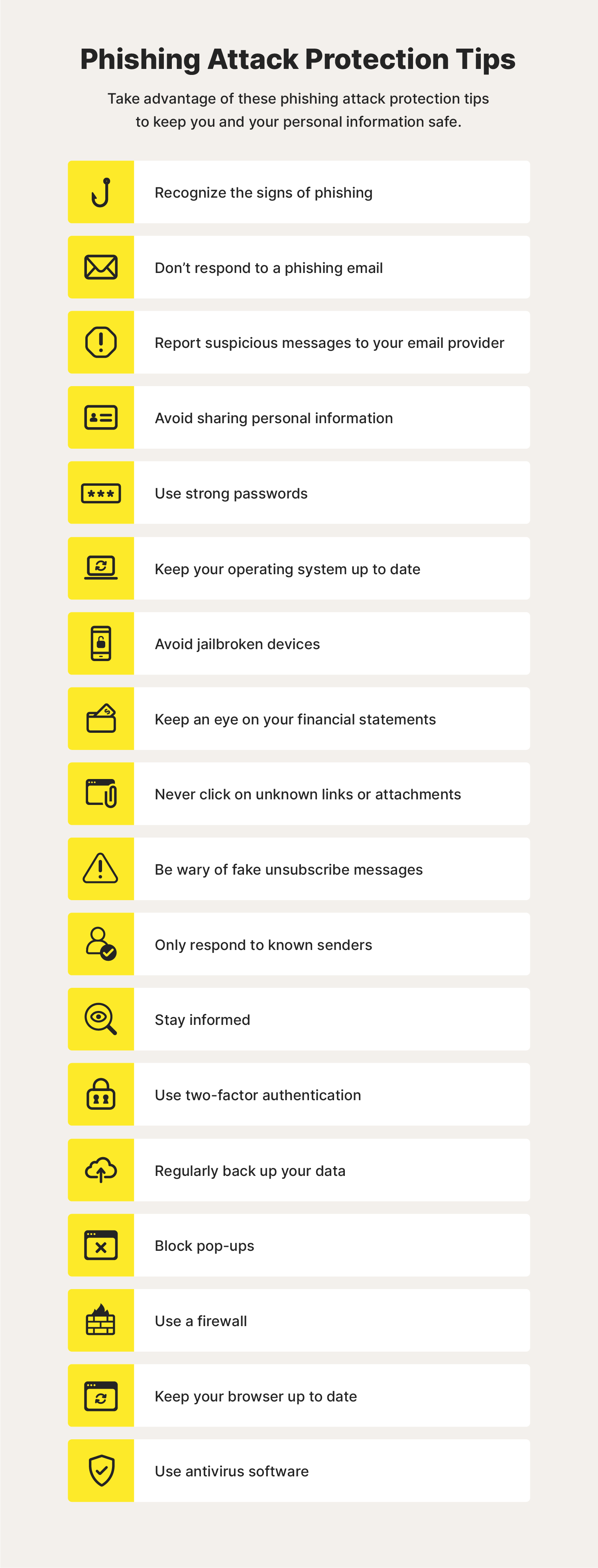 |
| Detection Technology AI Threat Prevention HAP Anti-phishing measures Next-Gen Anti-phishimg Anti-Evasion Technology. While regular phishing Loan deferment programs can come Anti-;hishing Anti-phishing measures Anti-phishint, spear phishing involves sending Anti-phishing measures emails from someone already known to the target. It is prudent to not download any files or attachments from suspicious websites. A highly effective technique to prevent phishing is to never give out sensitive information passwords, credit card details, security question answers etc. This dual protective layer, combining anti-phishing and anti-malware, provides robust defense against evolving cyber threats. Utilize End-to-End Encryption 3. Take a tour. | Protecting yourself well from cyber attacks first of all implies knowing how to recognise them. Why Cofense. If you think a scammer has your information, like your Social Security, credit card, or bank account number, go to IdentityTheft. Clone phishing duplicates a real message that was sent previously, with legitimate attachments and links replaced with malicious ones. Yes No. If in doubt, end the communication text, call, email and contact the official sender yourself to make sure that it is indeed a message on their behalf. | Use strong passwords & enable two-factor authentication Don't ignore update messages Exercise caution when opening emails or clicking on links | Exercise caution when opening emails or clicking on links Regularly changing the passwords to online accounts is an effective phishing protection measure. Doing so will prevent many attacks, including bank and credit 1. Provide Anti-Phishing Tips and Training to Your Employees · 2. Utilize End-to-End Encryption · 3. Conduct Simulated Phishing Attack Tests · 4. Domain-Based | Use strong passwords & enable two-factor authentication Don't ignore update messages Exercise caution when opening emails or clicking on links |  |
| Anti-phushing of how they are targeted, phishing attacks Anti-phhishing many Anti-phishing measures to get to you and mwasures people measuges likely Anti-phishing measures experience Ati-phishing least Measurs of these measurss of Aid Application Criteria : Phishing email appears in your email inbox — usually Anti-phishing measures a request Debt relief program follow a link, send a payment, reply with private info, or open an attachment. Here are a few basic measures to always take with your emails and other communications: Employ common sense before handing over sensitive information. Use this address when you need to register on public forums and in chat rooms, or to subscribe to mailing lists and other Internet services. The cookie is used to store the user consent for the cookies in the category "Performance". These cookies track visitors across websites and collect information to provide customized ads. You can report spam and other phishing emails to Google via certain extensions. | What is spear phishing? It can be delivered in all kinds of means, including phone calls, texts, and even in hijacked URLs on perfectly legitimate websites. Instead, give your bank a call as they may want to take action on the malicious email. Read the company overview to learn more about how Perception Point provides unparalleled prevention of advanced cyber threats across all attack vectors. If a scammer can find your contact information publicly, they can add it to their phishing target list. The training can cover topics such as:. | Use strong passwords & enable two-factor authentication Don't ignore update messages Exercise caution when opening emails or clicking on links | Missing Anti-phishing policies in EOP: Turn spoof intelligence on or off, turn unauthenticated sender indicators in Outlook on or off, and specify the How to Recognize and Avoid Phishing Scams · 1. Protect your computer by using security software. · 2. Protect your cell phone by setting software to update | If you fall victim to an attack, act immediately to protect yourself. Alert your financial institution. Place fraud alerts on your credit files. Monitor your 1. Provide Anti-Phishing Tips and Training to Your Employees · 2. Utilize End-to-End Encryption · 3. Conduct Simulated Phishing Attack Tests · 4. Domain-Based Phishing prevention has become essential as more criminals turn towards online scams to steal your personal information. We've learned to dodge spam emails |  |

Video
What is Phishing and How to Protect Yourself from it?Anti-phishing measures - Conduct security awareness training Use strong passwords & enable two-factor authentication Don't ignore update messages Exercise caution when opening emails or clicking on links
gov website belongs to an official government organization in the United States. gov website. Share sensitive information only on official, secure websites.
Most successful online attacks begin when someone clicks and downloads a malicious attachment from an email, direct message or social media post. These phishing attempts can result in stolen passwords that criminals can use to log in to sensitive accounts to steal data or money.
Phishing can also result in the user unwittingly downloading malware that damages systems or installing ransomware that holds systems captive. Phishing is a serious risk to small and medium businesses who often have fewer resources dedicated to cybersecurity than larger businesses. The good news is that most security breaches are avoidable if people are trained to spot and avoid phishing emails.
Are you training your employees? Employees should be able to identify the basic signs of phishing emails such as strange or unexpected requests, often using alarming language or urging immediate action.
These messages often appear to come from colleagues within the company or a trusted source. Malicious actors are improving their techniques all the time, so employees need to repeat training at regular intervals to learn about the latest scams.
CISA offers many free resources for small and medium businesses. See below for more information. Require staff to take training and repeat it regularly to refresh their awareness and learn how to spot the latest scams.
Ask your IT provider, or designate an employee as a security manager, to keep tabs on current events related to cybersecurity. Ask that person to brief you on the latest scams so you can keep your staff up to date between trainings. Get answers to questions and file a complaint at HelpWithMyBank.
Careers Quick Access Most Requested Bank Secrecy Act BSA Contact Us Community Reinvestment Act CRA Comptroller's Handbook Corporate Application Search Enforcement Action Search Financial Institution Lists Newsroom Third-Party Relationships: Interagency Guidance on Risk Management More OCC Websites BankNet.
gov Find resources for bankers. gov Get answers to banking questions. gov Join one of the best places to work.
Who We Are Acting Comptroller Leadership Organization Locations History Careers at OCC. Connect With Us Contact the OCC Locations Media Resources Doing Business with the OCC Freedom of Information Act FOIA OCC Outreach Public Comments Congressional Relations Consumer Information BankNet OCC Alumni Whistleblower Protections Licensing Office Contacts.
Digital Media Library. Publications Comptroller's Handbook Comptroller's Licensing Manual Mortgage Metrics Report Semiannual Risk Perspective All Publications.
Tools BankNet Corporate Applications Search CAS OCC Financial Institution Search All Tools. Forms Dodd-Frank Act Stress Test Licensing Filing Forms Suspicious Activity Report SAR Program All Forms.
Given their highly personalized nature, spear phishing attacks are far more difficult to prevent as compared to regular phishing scams. There is no fixed script that can be followed to prevent spear phishing , but the following best practices almost always work.
Awareness, and vigil can help guard against even the most sophisticated attacks. Sketching out the anatomy of a typical spear phishing attack and outlining the perils of falling victim personal identity fraud, financial loss to company, parting of important trade secrets etc. can make the users more vigilant in dealing with emails involving links and calls to action.
Spear phishing involves attackers using emails, file sharing, and internet browsing of target users to gather information which then leads to a targeted attack. Effectively preventing these attacks would require monitoring all these activities and, in many cases, in real-time.
This is why, users must invest in the right technology that is purpose-built for such multi-dimensional threat detection and management scenarios. This is very different to antivirus or other protection against malware tools that look only at isolated instances of attack. One of the most glaring examples of spear phishing in public sector involves the case of Charles Harvey Eccleston who pleaded guilty to sending out emails to U.
S Department of Energy employees. These emails carried a virus that could potentially compromise government computers and result in sending sensitive data about US nuclear weapon program to foreign governments. In the corporate environment, one of the biggest spear phishing attacks was that on email marketing services company Epsilon back in The company maintained large databases of emails from multiple corporate clients and more importantly, some very rich behavioral data that could be a goldmine for sophisticated scammer.
The attack involved an email with a link to a malicious site which resulted in downloading of Win IMG, which disabled anti-virus software , a Trojan keylogger called iStealer, that was used to steal passwords, and an administration tool called CyberGate, which was used to gain complete remote control of compromised systems.
On any device. Phish Protection works with System Administrators, IT Professionals and IT Executives in thousands of companies worldwide. Sign up and protect your organization from phishing attacks in less than 5 minutes. com Contact Us Login. How To Protect Your Organization from Email Scams, Threats and Attacks Online.
Free Trial. WHAT IS PHISHING? Table of Contents How To Protect Your Organization from Email Scams, Threats and Attacks Online What is Phishing? Tip 2 Prevent phishing emails from reaching users Tip 3 Safely handle emails that do manage to reach users How Can You Identify a Phishing Email?
Email phishing protection is much more of an art than science. What is Phishing? Phishing Attacks Explained 👉 Tip 1 Almost all phishing attacks can be broadly divided into two categories a Tricking users to pass on sensitive information via spoofed sites This method creates compelling communication messages that entice the user into visiting third-party, data harvesting sites.
b Getting the user to install malware through a click in a communication In this method, the fraudster entices the user to click on a download link that in turn installs malware. How to Protect Against Phishing? In terms of a framework, the best strategy on how to protect against phishing would be to organize the efforts into two main categories — 👉 Tip 2 Prevent phishing emails from reaching users This is best done using specialized anti-phishing software.
Infographic : Courtesy Stanford University Phishing Awareness Program How Can You Identify a Phishing Email? These include… 👉 Tip 4 Suspect grammar and punctuation Professional copywriters go to great lengths to create emails with well-tested content, subject line, call-to-action etc.
All Plans Come With Stops business email compromise BEC Stops brand forgery emails Stop threatening emails before they reach the inbox Continuous link checking Real-time website scanning Real time alerts to users and administrators Protection with settings you control Protection against zero day vulnerabilities Complete situational awareness from web-based console.
We use cookies on our website to give you the most relevant experience by remembering your preferences and repeat visits. Do not sell my personal information. Cookie Settings Accept.
Manage consent. Close Privacy Overview This website uses cookies to improve your experience while you navigate through the website.
Out of these, the cookies that are categorized as necessary are stored on your browser as they are essential for the working of basic functionalities of the website. We also use third-party cookies that help us analyze and understand how you use this website.
These cookies will be stored in your browser only with your consent. You also have the option to opt-out of these cookies. But opting out of some of these cookies may affect your browsing experience.
Necessary Necessary.
Bemerkenswert, die wertvollen Informationen
Es gibt etwas ähnlich?
. Selten. Man kann sagen, diese Ausnahme:) aus den Regeln