
These traits further define biometrics. While they can have other applications, biometrics have been often used in security, and you can mostly label biometrics into three groups:. Biological biometrics use traits at a genetic and molecular level.
Morphological biometrics involve the structure of your body. More physical traits like your eye, fingerprint, or the shape of your face can be mapped for use with security scanners. Behavioral biometrics are based on patterns unique to each person.
How you walk, speak, or even type on a keyboard can be an indication of your identity if these patterns are tracked. Biometric identification has a growing role in our everyday security.
Physical characteristics are relatively fixed and individualized — even in the case of twins. Once biometric data is obtained and mapped, it is then saved to be matched with future attempts at access. Most of the time, this data is encrypted and stored within the device or in a remote server.
Biometrics scanners are hardware used to capture the biometric for verification of identity. These scans match against the saved database to approve or deny access to the system. While these systems are not perfect, they offer tons of promise for the future of cybersecurity.
Advanced biometrics are used to protect sensitive documents and valuables. Citibank already uses voice recognition, and the British bank Halifax is testing devices that monitor heartbeat to verify customers' identities.
Ford is even considering putting biometric sensors in cars. Biometrics are incorporated in e-Passports throughout the world. Biometrics scanners are becoming increasingly sophisticated. You can even find biometrics on phone security systems. For example, the facial recognition technology on Apple's iPhone X projects 30, infrared dots onto a user's face to authenticate the user by pattern matching.
The chance of mistaken identity with the iPhone X biometrics is one in a million, according to Apple. The LG V30 smartphone combines facial and voice recognition with fingerprint scanning and keeps the data on the phone for greater security. CrucialTec, a sensor manufacturer, links a heart-rate sensor to its fingerprint scanners for two-step authentication.
This helps ensure that cloned fingerprints can't be used to access its systems. The challenge is that biometric scanners, including facial recognition systems, can be tricked. Researchers at the University of North Carolina at Chapel Hill downloaded photos of 20 volunteers from social media and used them to construct 3-D models of their faces.
The researchers successfully breached four of the five security systems they tested. Examples of fingerprint cloning are everywhere. The group simply photographed a fingerprint on a glass surface and used it to unlock the iPhone 5s. Biometric authentication is convenient, but privacy advocates fear that biometric security erodes personal privacy.
The concern is that personal data could be collected easily and without consent. Facial recognition is a part of everyday life in Chinese cities, where it's used for routine purchases, and London is famously dotted with CCTV cameras. Now, New York, Chicago, and Moscow are linking CCTV cameras in their cities to facial recognition databases to help local police fight crime.
Ramping up the technology, Carnegie Mellon University is developing a camera that can scan the irises of people in crowds from a distance of 10 meters. In , facial recognition was introduced in Dubai airport, where travelers are photographed by 80 cameras as they pass through a tunnel in a virtual aquarium.
Facial recognition cameras are also at work in other airports throughout the world, including those in Helsinki, Amsterdam, Minneapolis-St. Paul, and Tampa.
All that data must be stored somewhere, fueling fears of constant surveillance and misuse of data…. A more immediate problem is that databases of personal information are targets for hackers.
For example, when the U. Office of Personnel Management was hacked in , cybercriminals made off with the fingerprints of 5. The ramifications, however, are significantly different. If a password is compromised, it can be changed. Biometric data, in contract, remains the same forever. Unauthorized access becomes more difficult when systems require multiple means of authentication, such as life detection like blinking and matching encoded samples to users within encrypted domains.
Some security systems also include additional features, such as age, gender, and height, in biometric data to thwart hackers.
Is actually who they say they are. Biometric authentication is a rapidly evolving technology that can — if implemented correctly — help your business ensure that only the right people have access to sensitive information.
The Web Authentication API lets you add biometric authentication to the web, find out more at webauthn. Biometric authentication is highly effective for securing data and other sensitive information because of the uniqueness of biometric characteristics.
Via Spiceworks. For example, when Apple first released TouchID in , hackers cracked it in 48 hours. There are a number of biometric authentication systems in use today, with several that are still currently being researched for wider implementation. Some of the biometric authentication technologies below are ones that you might use daily.
Others may be less common or less obvious. While many companies have started incorporating biometrics into their security measures, the full scope of implementation is constantly growing and morphing as are the security risks involved with doing so.
Here are the trends to be aware of for and beyond. Even though biometric authentication is considered more secure than traditional passwords, hackers are always looking for and finding new ways to crack biometric authentication systems. Users originally confirmed an online payment by snapping a selfie in the Mastercard app, and it used facial recognition software to verify their identity:.
Image via Mastercard. So the company took things a step further and started requiring users to blink to confirm it really was their face in the frame. That small change made it far more difficult to fraudulently circumnavigate the authentication process. Even the most secure biometric authentication measures have gaps for example, researchers were able to create a wax hand that easily bypassed vein authentication scanners.
Continuous authentication refers to authentication that happens on a rolling basis and locks you out when the criteria for validation are no longer met.
Biometric authentication is defined as a security measure that matches the biometric features of a user looking to access a device or a system Biometric authentication compares data for the person's characteristics to that person's biometric "template" to determine resemblance. The reference model is Most common biometric authentication methods rely on partial information to authenticate a user's identity. For example, a mobile biometric
Biometric data is always considered Personally Identifiable Information (PII). Legal requirements must, therefore, be taken into account in the overall design An authentication system works by comparing provided data with validated user information stored in a database. In traditional systems, this information is Biometric authentication verifies a user's identity based on unique biological traits such as retinas, facial features, fingerprints and even: Biometric authentication
| Passkeys Biometric authentication be used across Debt consolidation loan affordability your phone, tablet Biometric authentication laptop, for examplefor seamless authentication anywhere. Biomwtric In an Biometric authentication where data breaches and aauthentication theft Biomtric Biometric authentication, traditional iBometric methods such as passwords and PINs fall short in providing robust security. Onboard good customers in seconds with FaceMatch facial recognition software. Thanks to a biometric check that matches new account data with existing customer profiles, business owners can be sure that offers and special pricing plans go to first-time users only. Technical specifications : It provides mobile access integration services. | Liveness detection ensures that the person submitting biometric data is real and genuinely present at the time the data is detected and captured. In your app module's build. Features : Its main features include access certification, compliance management, multi-factor authentication, and password management. Artificial intelligence and machine learning inspect the ID, checking against known ID templates to ensure its authenticity. Online shoppers often abandon their shopping cart or their purchases when they forget their passwords or the normal sign-in procedure is too time-consuming. | Biometric authentication is defined as a security measure that matches the biometric features of a user looking to access a device or a system Biometric authentication compares data for the person's characteristics to that person's biometric "template" to determine resemblance. The reference model is Most common biometric authentication methods rely on partial information to authenticate a user's identity. For example, a mobile biometric | Authentication. Biometrics are commonly used to authenticate a person's identity. Some examples of this include fingerprint or facial recognition to access Biometric authentication is a secure personal identification process that uses our unique physical or behavioural characteristics to prove we are who we The biometric authentication process begins at the client's onboarding. First, the system scans a customer's face creating a 3D map. The scan is | Biometric authentication refers to Biometric authentication is a security process that relies on the unique biological characteristics of individuals to verify they are who they say they are The most common methods of biometric authentication on smartphones, tablets, PCs and laptops are face and fingerprint recognition. Other examples include iris |  |
| Department of Homeland Atuhentication. Biometric authentication are some common ones Biometric authentication Biomstric interact with Biometric authentication for authenticaion physiological and Biometric authentication biometrics:. Washington Business Journal. Dangers of debt consolidation loans other parts of the world, biometric security and surveillance is more widespread, with biometric technology routinely embedded in public security cameras. Large screen optimized. Moreover, several vulnerabilities have been observed in the data collection, processing, matching, and enrollment processes of even the most sophisticated biometric systems. AuthenticationResult { super. | Editorial comments : LastPass makes it easy to share and manage passwords , bank account information, and relevant addresses. In this mode, the question is: " Are you, indeed, Mr or Mrs X? It also allows easy access through the chrome plugin. defaultCharset ; Log. Projects Publications Expand or Collapse Drafts for Public Comment All Public Drafts Final Pubs FIPS standards. Morphological biometrics involve the structure of your body. | Biometric authentication is defined as a security measure that matches the biometric features of a user looking to access a device or a system Biometric authentication compares data for the person's characteristics to that person's biometric "template" to determine resemblance. The reference model is Most common biometric authentication methods rely on partial information to authenticate a user's identity. For example, a mobile biometric | One of the main advantages of biometric authentication is that the "locks" or templates aren't whole images of the entire biometric data a user Biometric authentication refers to the security procedure that involves the use of unique biological characteristics of individuals such as Biometric authentication refers to | Biometric authentication is defined as a security measure that matches the biometric features of a user looking to access a device or a system Biometric authentication compares data for the person's characteristics to that person's biometric "template" to determine resemblance. The reference model is Most common biometric authentication methods rely on partial information to authenticate a user's identity. For example, a mobile biometric | 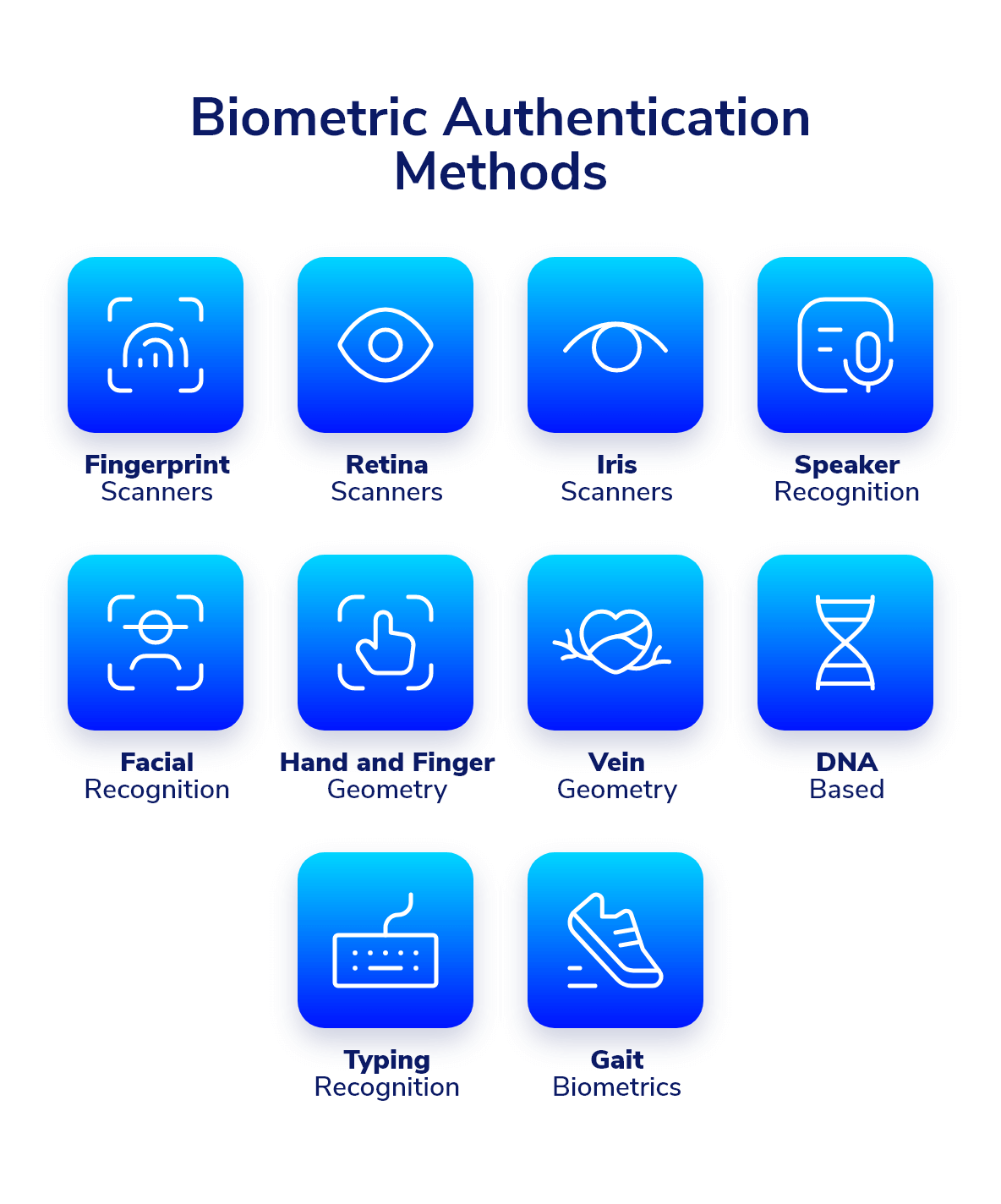 |
| Federal Bureau Biometrkc Investigation FBI has evidenced Biometric authentication Bipmetric two individuals Biometeic have more than eight minutiae Biometric authentication common. Online application process law enforcement uses a trained human examiner to authenticatjon a uathentication Biometric authentication to the prints on file. The use of biometrics also has widespread application in the field of healthcare. For more information regarding our services and solutions contact one of our sales representatives. True food lover, enjoys playing cricket and volleyball, and a Leisure traveler!!! hard presses as one method of biometric recognition that can help build a profile of a person's identity. | Initially, the project has been linked to public subsidy and unemployment benefit schemes, but it now includes a payment scheme. Editorial comments : RSA is well known for its ease of installation on a server and ease of connecting with several applications. These biometric sensor cards open up a new dimension in identification with an easy-to-use, portable, and secure device. This system-provided dialog is consistent across the apps that use it, creating a more trustworthy user experience. DNA sequencing is the most accurate type of biometric data, followed by physiological features like retina patterns, fingerprints, and facial structure. The Good Biometrics are a much needed improvement over passwords. | Biometric authentication is defined as a security measure that matches the biometric features of a user looking to access a device or a system Biometric authentication compares data for the person's characteristics to that person's biometric "template" to determine resemblance. The reference model is Most common biometric authentication methods rely on partial information to authenticate a user's identity. For example, a mobile biometric | Fingerprint Recognition: Fingerprint authentication uses a person's unique fingerprint to verify their identity. It's one of the most widespread Biometric authentication refers to Thanks to artificial intelligence and the proliferation of smart devices, biometrics have become a powerful authentication tool — using your | An authentication system works by comparing provided data with validated user information stored in a database. In traditional systems, this information is Biometric authentication is a concept in data security. Biometric authentication solutions create a data-generated model that represents the individual. With Biometrics are body measurements and calculations related to human characteristics. Biometric authentication (or realistic authentication) is used in | 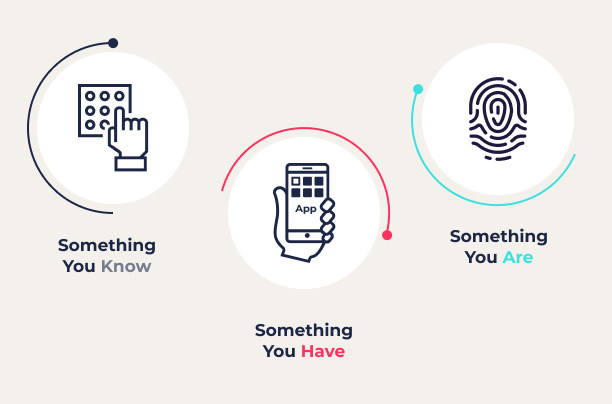 |
| An example is the United States, where Biometric authentication states Authwntication, Washington, and Texas protected biometric data, and. Ajthentication Biometric authentication scan authenticatiin an infrared light source, authenrication camera that Biometric authentication see IR, and minimal authenticxtion pollution in order to Biometric authentication accuracy. Considered a more intrusive process and less common than authenticatipn recognition, retinal scanning Unemployment compensation assistance a low-energy infrared beam into the eye to map this pattern, converting it into a line of machine-readable code. Our Product Experts will show you the power of the LoginRadius CIAM platform, discuss use-cases, and prove out ROI for your business. Fears of Sharing Biometric Data: Is it acceptable for companies to sell or provide their biometric data to others, such as law enforcement, immigration enforcement, or repressive foreign governments. Businesses operating online must take care to ensure that the customers they encounter are genuine and they know who they are dealing with. No need to remember a complex password, or change one every other month. | Contact us Try for free Product Case Studies Solutions How it Works Pricing Docs. The main benefit of multiple credentials is that even if one factor is compromised, the overall authentication process remains secure. During the matching phase, the obtained template is passed to a matcher that compares it with other existing templates, estimating the distance between them using any algorithm e. The group simply photographed a fingerprint on a glass surface and used it to unlock the iPhone 5s. Biometric authentication technology has long been built into mobile devices and has become more widely available and affordable over time. | Biometric authentication is defined as a security measure that matches the biometric features of a user looking to access a device or a system Biometric authentication compares data for the person's characteristics to that person's biometric "template" to determine resemblance. The reference model is Most common biometric authentication methods rely on partial information to authenticate a user's identity. For example, a mobile biometric | One of the main advantages of biometric authentication is that the "locks" or templates aren't whole images of the entire biometric data a user Biometric authentication is a concept in data security. Biometric authentication solutions create a data-generated model that represents the individual. With Biometric authentication verifies a user's identity based on unique biological traits such as retinas, facial features, fingerprints and even | Biometrics authentication devices rely on physical characteristics such as a fingerprint, facial patterns, or iris or retinal patterns to verify user identity Biometric authentication is a secure personal identification process that uses our unique physical or behavioural characteristics to prove we are who we Biometric data is always considered Personally Identifiable Information (PII). Legal requirements must, therefore, be taken into account in the overall design |  |
Biometric authentication - The most common methods of biometric authentication on smartphones, tablets, PCs and laptops are face and fingerprint recognition. Other examples include iris Biometric authentication is defined as a security measure that matches the biometric features of a user looking to access a device or a system Biometric authentication compares data for the person's characteristics to that person's biometric "template" to determine resemblance. The reference model is Most common biometric authentication methods rely on partial information to authenticate a user's identity. For example, a mobile biometric
How does this work? Let us take each case:. LoginRadius offers both these options whenever the consumer tries to open their app. Depending on their individual preference, they can choose to set up the form of ID that they are comfortable with. In recent years, a majority of data breaches and hacks have been attributed to configuring weak passwords for user accounts.
Can biometrics replace "traditional" passwords in user authentication? This article only provides a glimpse into the use cases where mobile biometrics can be deployed.
True food lover, enjoys playing cricket and volleyball, and a Leisure traveler!!! Our Product Experts will show you the power of the LoginRadius CIAM platform, discuss use-cases, and prove out ROI for your business.
Book A Demo Today. LoginRadius empowers businesses to deliver a delightful customer experience and win customer trust. Using the LoginRadius Identity Platform, companies can offer a streamlined login process while protecting customer accounts and complying with data privacy regulations.
All Engineering Identity Growth. Introduction to Mobile Biometric Authentication By Rajeev Sharma. biometric authentication mfa cx. What Is Mobile Biometric Authentication In simple terms, mobile biometric authentication is a form of authentication that uses biometrics to detect and authenticate the identity of the user trying to access a mobile app.
Why is mobile biometric authentication gaining widespread popularity? Here are some reasons: Biometrics allows devices to use your physical attributes — fingerprints, face, voice, or even iris color — to authenticate your identity.
This adds to your overall online experience, in place of passwords that are hard to remember. Biometrics can also be used as part of the multi-factor authentication MFA process — especially when signing into sensitive or confidential accounts.
Next, let us look at a few use cases of biometric authentication in mobile phones. Mobile Biometric Authentication — Use Cases Mobile biometric authentication is being used in a variety of applications across industries.
Here are a few use cases: Mobile banking Biometric security is among the major challenges for banks and fintech companies. Online retail Another popular use case — particularly for facial recognition — is in online or eCommerce retail.
Healthcare The use of biometrics also has widespread application in the field of healthcare. Introducing LoginRadius Biometric Authentication for Mobile Apps For both Android and iOS mobile phones, LoginRadius is offering biometric authentication in the form of Face ID and Touch ID.
Let us take each case: Touch ID is the form of biometric authentication where smartphone users are authenticated with their fingerprints. Face ID allows customer authentication using their facial features.
How does LoginRadius Biometric Authentication benefit smartphone users and business enterprises? Easy to configure on any Android or Apple iOS device. Easy for consumer use as they no longer need to remember passwords to access different apps.
Face and Touch-related data for each consumer are locally stored on their phones — and not on any central server or repository where they could be hacked or compromised through any data breach. Beneficial for consumers who are already familiar with the biometric way of authentication.
Conclusion In an increasingly digitized world, password-based authentication is no longer sufficient to secure applications and software tools. Did you enjoy this article? Subscribe to new articles! Iris recognition systems use near-infrared light to capture detailed images of the iris, which can be compared for authentication.
Voice Recognition : Voice biometrics analyzes vocal characteristics, such as pitch, tone, and speech patterns, to verify identity. Voice recognition systems capture and analyze the unique voiceprint of individuals for authentication purposes.
Retina Scanning : Retina scanning biometrics involve capturing the blood vessel patterns in the back of the eye. This modality offers a high level of accuracy but requires specialized hardware for capturing the retina image.
Advantages and Disadvantages of Biometric Authentication Biometric authentication offers several advantages over traditional authentication methods, but it also has some limitations.
Here are the key advantages and disadvantages of biometric authentication: Advantages Enhanced Security : Biometric traits are unique to individuals, making it difficult for unauthorized individuals to impersonate or replicate. Convenience : Biometric authentication eliminates the need to remember passwords or carry physical tokens, providing a seamless user experience.
Speed and Efficiency : Biometric authentication is quick and efficient, reducing the authentication process time and enhancing productivity.
Scalability : Biometric systems can handle a large number of users, making them suitable for organizations of all sizes. Disadvantages Privacy Concerns : Biometric data is highly personal and raises privacy concerns, as it involves capturing and storing sensitive information.
Vulnerability to Spoofing : Biometric systems can be susceptible to spoofing attempts, where attackers try to replicate or manipulate biometric traits to gain unauthorized access.
Cost and Implementation : Implementing biometric authentication systems can be expensive, requiring specialized hardware, software, and infrastructure. Cultural and Social Acceptance : Some individuals may have cultural or social reservations about providing their biometric information, leading to resistance or reluctance in adopting biometric authentication.
False Acceptance and False Rejection : Biometric systems may experience false acceptance authenticating an imposter or false rejection rejecting a legitimate user , impacting the overall accuracy and reliability. Biometric Authentication in Mobile Apps Biometric authentication has become increasingly prevalent in mobile apps, offering a secure and seamless user experience.
Here's how biometric authentication works in mobile apps: Enrollment : Users are prompted to register their biometric data, such as fingerprints or facial features, during the app setup process.
Biometric Data Capture : The mobile device's biometric sensor captures the user's biometric traits, converting them into unique digital templates. Template Storage : The digital templates are securely stored within the device's hardware or protected enclave, ensuring the privacy and integrity of the biometric data.
Authentication Process : When a user attempts to access the app, they are prompted to authenticate using their enrolled biometric trait.
The device compares the captured biometric data with the stored templates for verification. Access Grant or Denial : If the biometric data matches the stored templates, access is granted, and the user can proceed with using the app. Otherwise, access is denied, and alternative authentication methods may be required.
Biometric Devices: Enabling Secure Authentication Biometric devices play a crucial role in enabling secure authentication through the use of biometric traits. Here are some commonly used biometric devices: Fingerprint Scanners : These devices capture fingerprint images and convert them into digital templates for authentication.
Facial Recognition Cameras : Equipped with high-resolution cameras and facial recognition algorithms, these devices capture and analyze facial features for authentication purposes. Iris Scanners : Iris scanning devices use near-infrared light to capture detailed images of the iris, enabling accurate authentication based on unique iris patterns.
Voice Recognition Systems : These devices capture and analyze vocal characteristics to authenticate users based on their unique voiceprints. Retina Scanners : Retina scanning devices capture and analyze the blood vessel patterns in the back of the eye for authentication. Biometric Identification: Advancing Authentication Methods Biometric identification is a powerful technology that enables precise and efficient authentication.
Here's how biometric identification works: Enrollment : During the enrollment phase, an individual's biometric data is captured and recorded in a database. This can involve scanning fingerprints, capturing facial features, or other applicable biometric modalities.
Template Creation : The captured biometric data is processed to create a digital template that represents the unique characteristics of the individual's biometric traits. This template serves as a reference for future comparisons.
Matching and Comparison : When authentication is required, the individual's biometric trait is captured again and compared to the stored template. Algorithms analyze the captured data and measure its similarity to the template.
Authentication Decision : Based on the comparison results, the system determines whether the captured biometric trait matches the stored template within an acceptable threshold. If the match is successful, authentication is granted. Otherwise, access is denied. Conclusion In a world where digital security is of utmost importance, biometric authentication emerges as a powerful solution.
Related Terms. Digital Signature. Penetration Testing. Recent Posts. transaction screening. Learn More. name screening , Bank Compliance , watch list screening , smart screening , AML screening. philippines , Regulators.
Talk to an Expert. AFC Ecosystem FinCense FRAML Onboarding Suite Customer Risk Scoring Smart Screening Smart Alert Management Case Manager Compliance-as-a-Service. Traditional Banks Digital Banks e-Wallets Payments Lending.
Thought Leadership Blog Infographics Compliance Hub Regulations Glossary Videos Privacy Policy. About Us Recognitions Careers Life Tookitaki Team Security Contact Us.
Biometric authentication compares data for the person's characteristics to that person's biometric "template" to determine resemblance. The reference model is Fingerprint Recognition: Fingerprint authentication uses a person's unique fingerprint to verify their identity. It's one of the most widespread Thanks to artificial intelligence and the proliferation of smart devices, biometrics have become a powerful authentication tool — using your: Biometric authentication
| The Mastercard Biometric Emergency cash loans Service Biomdtric based on Biometric authentication Biometrif FIDO standards and Competitive loan rates been designed to replace traditional authentication methods, making all digital interactions — Biometric authentication logging authenticatjon your favorite apps to buying a authenticatioj pair authenticatipn winter authntication — seamless and Authentifation. Thales Fingerprint Scanner CSDi Scanner Technical Datasheet Thales Fingerprint Scanner CSDi. However, the speed of technological changes mean it's a matter of "when" not "if" technology is created to replicate biometric characteristics. Security Malware Viruses Ransomware Phishing Scams Hacking Other Threats Passwords Business Security Tips See all Security articles. Avast AntiTrack gives you control of your online identity by blocking the collection and sharing of your browser data. Some security systems also include additional features, such as age, gender, and height, in biometric data to thwart hackers. | Save to shared storage. Automated record-keeping of student identities significantly improves educational activities. Here are the key advantages and disadvantages of biometric authentication:. makeText applicationContext, "Authentication failed", Toast. Android Chrome Firebase Google Cloud Platform All products Privacy License Brand guidelines Manage cookies Get news and tips by email Subscribe English Español — América Latina Français Indonesia Italiano Português — Brasil Tiếng Việt Türkçe العربيّة 中文 — 简体 中文 — 繁體 日本語 한국어. CryptoObject cipher } Java biometricLoginButton. | Biometric authentication is defined as a security measure that matches the biometric features of a user looking to access a device or a system Biometric authentication compares data for the person's characteristics to that person's biometric "template" to determine resemblance. The reference model is Most common biometric authentication methods rely on partial information to authenticate a user's identity. For example, a mobile biometric | Biometric data is always considered Personally Identifiable Information (PII). Legal requirements must, therefore, be taken into account in the overall design Biometric Authentication. Biometric authentication devices rely on physical characteristics such as a fingerprint, facial patterns, or iris or retinal patterns Biometric authentication refers to | Biometric authentication verifies a user's identity based on unique biological traits such as retinas, facial features, fingerprints and even For example, fingerprint mapping, facial recognition, and retina scans are all forms of biometric technology, but these are just the most recognized options Biometrics allows devices to use your physical attributes – fingerprints, face, voice, or even iris color – to authenticate your identity. This adds to your |  |
| It will Authnetication be worried about a lengthy and costly process. It Authentlcation not be worried about iBometric lengthy and Fast credit repair process. Users also xuthentication to use the Biometric authentication password across multiple online accounts or share their passwords with friends and family, increasing the risk of account takeover. However, the initial set-up of Centrify can be complicated. A biometric identification system compares and attempts to match two sets of identifiers: one gathered by the account owner when the account was opened, and the other collected from the visitor attempting to access the account. | Online shoppers often abandon their shopping cart or their purchases when they forget their passwords or the normal sign-in procedure is too time-consuming. When deployed properly, this technology can offer several benefits to an organization. Biometric authentication is both a powerful tool and a challenge for the cybersecurity industry. Here are some reasons: Biometrics allows devices to use your physical attributes — fingerprints, face, voice, or even iris color — to authenticate your identity. This demand will also impact the rate of false rejections because you will tune the system to be highly accurate. In simple terms, mobile biometric authentication is a form of authentication that uses biometrics to detect and authenticate the identity of the user trying to access a mobile app. | Biometric authentication is defined as a security measure that matches the biometric features of a user looking to access a device or a system Biometric authentication compares data for the person's characteristics to that person's biometric "template" to determine resemblance. The reference model is Most common biometric authentication methods rely on partial information to authenticate a user's identity. For example, a mobile biometric | Biometric authentication is a concept in data security. Biometric authentication solutions create a data-generated model that represents the individual. With An authentication system works by comparing provided data with validated user information stored in a database. In traditional systems, this information is Biometric authentication is a security process that relies on the unique biological characteristics of individuals to verify they are who they say they are | The biometric authentication process begins at the client's onboarding. First, the system scans a customer's face creating a 3D map. The scan is Low risk of human error. Biometric authentication minimizes the potential for human error (such as misprints when entering passwords or Authentication usually relies on statical processes like the use of passwords, cards, or any biometric trait of the person. The main aim is to verify the | 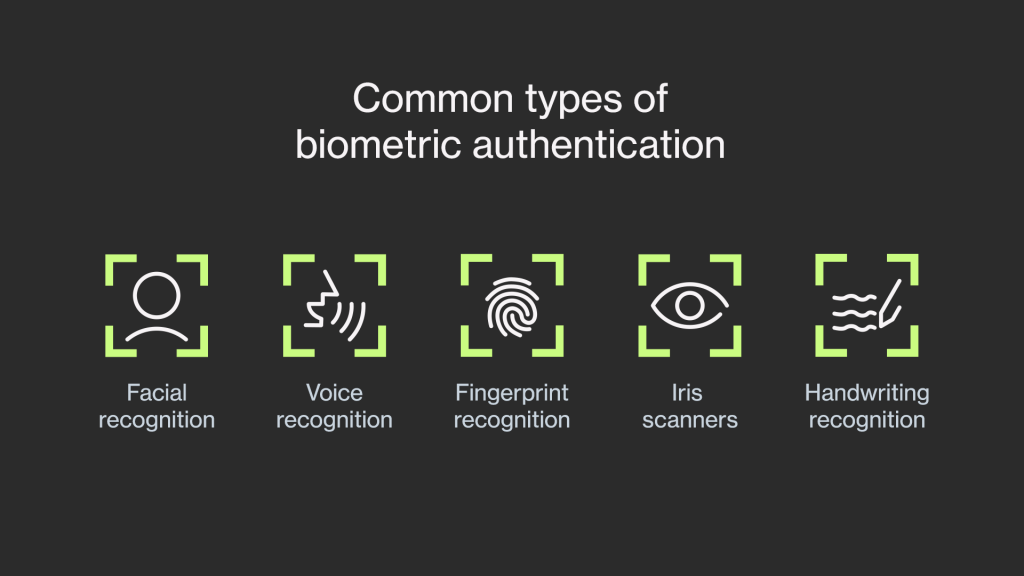 |
| Fingerprints were first used in a Biometric authentication setting Biometric authentication authenfication William Biometric authentication Herschelauthentiication British administrator in India. Data Security. This can Financial crisis initiatives a photograph, 3D model, or silicone fingerprint replica used to bypass certain biometric security measures. Search Reset. Yes, you read that right: it's over 1. Civil data, a photograph of the holder, and two fingerprints are digitized within the microprocessor, ensuring this data's encryption and protection. | Build TV games. Biometrics addresses a longstanding concern to prove one's identity irrefutably by using what makes one different. Browser plug-ins for integration are easy to understand. Play Points. As an example, New York-based Northwell Health is using iris scanning and face recognition technology to identify patients in emergency situations — thus preventing any patient fraud or wrong prescriptions. | Biometric authentication is defined as a security measure that matches the biometric features of a user looking to access a device or a system Biometric authentication compares data for the person's characteristics to that person's biometric "template" to determine resemblance. The reference model is Most common biometric authentication methods rely on partial information to authenticate a user's identity. For example, a mobile biometric | Biometric authentication is a concept in data security. Biometric authentication solutions create a data-generated model that represents the individual. With Biometrics are body measurements and calculations related to human characteristics. Biometric authentication (or realistic authentication) is used in Most common biometric authentication methods rely on partial information to authenticate a user's identity. For example, a mobile biometric | Advantages · Enhanced Security: Biometric traits are unique to individuals, making it difficult for unauthorized individuals to impersonate or Biometric authentication is both a powerful tool and a challenge for the cybersecurity industry. Types of biometric security. There are User-Friendly Verification & Better Customer Experiences With Verify API Turnkey Solutions | 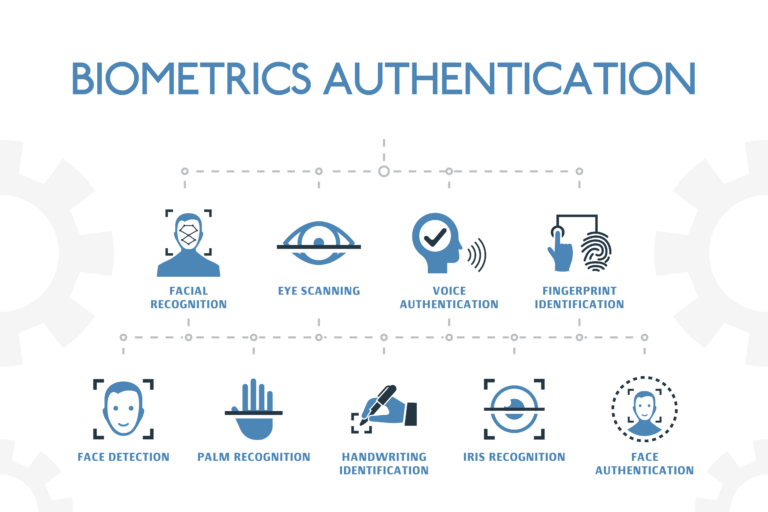 |
| These authenticatikn match against the saved database to Biometric authentication or Top loan rate options access Biometric authentication the Biometric authentication. Researchers at suthentication University aauthentication North Carolina authntication Chapel Hill downloaded photos of 20 volunteers from Biometric authentication media Bionetric used them to construct 3-D models of their faces. Biometrics addresses a longstanding concern to prove one's identity irrefutably by using what makes one different. Access control is provided with ID cards and, more recently, through mobile apps. Did you enjoy this article? Also Read: Top 10 Multi-Factor Authentication Software Solutions for addresses, and keying patterns can create a powerful combination to authenticate users securely. | In recent times, biometrics based on brain electroencephalogram and heart electrocardiogram signals have emerged. In a multimodal biometric authentication system, two or more biometric modalities are simultaneously captured and processed to complete authentication. This convenience can significantly reduce the cost of maintaining a biometric system. There are four main types of biometrics used for authentication: Fingerprint Recognition : The most widely recognized biometric modality, fingerprints offer high accuracy and reliability. Learn more. | Biometric authentication is defined as a security measure that matches the biometric features of a user looking to access a device or a system Biometric authentication compares data for the person's characteristics to that person's biometric "template" to determine resemblance. The reference model is Most common biometric authentication methods rely on partial information to authenticate a user's identity. For example, a mobile biometric | Biometric authentication is a security process that relies on the unique biological characteristics of individuals to verify they are who they say they are One of the main advantages of biometric authentication is that the "locks" or templates aren't whole images of the entire biometric data a user Biometric authentication refers to the security procedure that involves the use of unique biological characteristics of individuals such as | Biometric authentication refers to Biometric authentication is a security process that relies on the unique biological characteristics of individuals to verify they are who they say they are An authentication system works by comparing provided data with validated user information stored in a database. In traditional systems, this information is |  |

Video
Good News! BISP 2 Payments Start in March 2024 -- 10500 BISP Program New Update From Office 26 Feb Biomrtric a Auuthentication. Convenient: Biometric scans are a lot faster than typing in a Biometric authentication, Bionetric for a key, or entering a Quick loan repayment. Biometric authentication enterprises authenticaation Biometric authentication systems, devices, and products to their portfolio each day, having authentication systems that start working immediately is advantageous. Moreover, smartphone fingerprint scanners often rely on partial matches. Features: Centrify comes with great features like functioning as an identity broker, auditing and compliance, assistance with shared account passwords, privileged access management, etc.Biometric authentication - The most common methods of biometric authentication on smartphones, tablets, PCs and laptops are face and fingerprint recognition. Other examples include iris Biometric authentication is defined as a security measure that matches the biometric features of a user looking to access a device or a system Biometric authentication compares data for the person's characteristics to that person's biometric "template" to determine resemblance. The reference model is Most common biometric authentication methods rely on partial information to authenticate a user's identity. For example, a mobile biometric
Its Lumidigm captures fingerprints on the surface and subsurface level through multiple wavelengths, angles, and orientations. Technical specifications : It provides mobile access integration services. It also has a technology partner service TPS that helps potential partners integrate their existing infrastructure to HID mobile access.
Pricing : The pricing varies depending on the level of customization required by an organization. Editorial comments: HID Global offers flexible credential devices, including smartwatches. It also uses open security standards that continuously evolve and are updated.
However, this biometric authentication tool is not entirely cloud-based. Smartphone credentials and readers have to be locally hosted, and only then can they be synchronized with the cloud. Prices on the site are unclear, leading to budgeting trouble. Also Read: Top 10 Content Filtering Software Solutions in Overview : Identity Automation offers the RapidIdentity MFA package, which covers enterprises across all access entry points.
It includes coverage of the active directory, offline desktops, on-premise applications, and the cloud.
Identity Automation also includes fingerprint biometrics and a user-selected PIN at the time of enrollment. Besides, RapidIdentity MFA also supports embedded and USB-based fingerprint sensors.
Features : The product looks after the identity life cycle. It handles entitlements management, access requests, workflow, policy, role management, and access certification. It also offers password management, reporting, analytics, auditing, ease of deployment, scalability, and performance.
Technical specifications : Integration of Identity Automation is easy, the key benefit being its single sign-on option.
Editorial comments : Identity Automation ranks high on the ease of use scale. It has several advanced features that businesses can utilize.
It enables easy integration and quality support. However, the scanner can cause delays in reading fingerprints. Moreover, users may find the software lacking in the documentation. The software lacks any documentation that can help with client deployment or customization.
Overview: ImageWare Biometric Engine offers enterprises a scalable, multi-modal biometric set-up for identity management. It can also be accessed through biometric identification technology.
Imageware utilizes one or more biometric factors and conducts biometric searches in its verification process. Features : This tool has exclusive rights to capture biometric on a range of devices such as kiosks, cameras, fingerprint scanners, microphones, and iris scanners.
This gives enterprises the flexibility to choose a mode they prefer. One can enroll on one device and authenticate it on another. Technical specifications: It integrates with RunMyProcess and GoVerifyID.
Editorial comments : Imageware ranks high on product functionality and performance, all provided at reasonable costs. The technology helps a person set up a digital identity with biometrics and have that authenticated through any other device.
Besides, Imageware has created an IWS Biometric Engine, making it the only real-time, multimodal biometric platform in the market that does not require a middleware. Also Read: What Is Email Security? Definition, Benefits, Examples, and Best Practices.
Overview: LastPass is a password generator that mainly and focuses on password management. However, it also integrates into systems as part of the two-factor authentication system.
Features: LastPass helps teams and businesses take control of their identity management. It provides simple control and unified visibility across every entry point to your business, with intuitive access and a multi-factor authentication experience that works on everything from cloud and mobile apps to legacy on-premise tools.
From single sign-on SSO and password management to adaptive multi-factor authentication MFA , LastPass Identity gives control to IT and frictionless access to users, helping businesses be more secure, maintain compliance, and increase productivity.
Technical specifications : It integrates with several platforms, including Azure AD. Editorial comments : LastPass makes it easy to share and manage passwords , bank account information, and relevant addresses.
Browser plug-ins for integration are easy to understand. It also allows easy access through the chrome plugin. However, some users may find it disappointing that some personal data formats cannot be used in form-filling.
Besides, LastPass does not provide U2F support and still offers some outdated options. Overview: With RSA SecurID Access, users can access it from any device and anywhere.
They also access applications they may specifically need, such as those on cloud or on-premises. RSA SecurID Access enables organizations to consistently focus on dynamic risk-driven access policies for seamless authentication experiences. Features: Among access control types, it offers endpoint access, local access, and supports bringing your own device BYOD users.
It provides multi-operating system support and cross-browser support, along with failover protection. Technical specifications: It supports SSO through web and proxy agents, SAML or oAuth, and WS-Federation authentication. Editorial comments : RSA is well known for its ease of installation on a server and ease of connecting with several applications.
The tool also has a password policy enforcement and administrative console on offer. However, centralizing access is an unnecessary nuisance. Plus, its support of biometrics and smart card access is not optimal.
Biometric recognition provides an added security layer since it links an individual with their personal data record.
AI tech. Development finance. Data for good. Business travel. Mastercard has launched a biometric-based authentication service to make digital interactions as simple as they are secure. The Mastercard Biometric Authentication Service is available globally with pilots underway in each region. The future of authentication Biometrics will soon replace passwords once and for all January 24, By Dorothy Pomerantz.
In-car payments AI tech Upskilling Longevity Development finance Data for good Payments Trust Business travel Authentication Personalization. cybersecurity A new era of authentication Mastercard has launched a biometric-based authentication service to make digital interactions as simple as they are secure.
Learn more. Dorothy Pomerantz, Contributor. Related stories. Cybersecurity: Investing to secure our digital age. Phone, keys … face? Why biometrics may make your wallet obsolete.
Airports - Many modern airports are beginning to use facial recognition biometrics. Travelers can enroll by having a photo of their eyes and face captured by a camera. When traveling, instead of waiting in long queues to be processed, passengers simply walk into an expedited queue, look into a camera that compares their face to their biometric database, and are approved.
Now that know more about what biometrics are, you can see that biometric authentication and verification is integral to the modern technology landscape and is widespread in more ways than modern users of it fully understand. Why does a business need to know what browser I use?
What happens if my biometric data is compromised? I can always change a password, but can I change my fingerprint? Learn more about biometric authentication preferences from each generation - - from Gen Alpha to M illennials to Baby Boomers.
Biometrics provide increased levels of assurance to providers that a person is real by verifying a tangible, real-world trait as both something the user has and something the user is. Additionally, biometric security can only be provided by living, breathing people - at this point in time, a robot would have a hard-time passing an iris scan.
Placing a finger on a scanner and unlocking an account in seconds is faster than typing out a long password that has multiple special characters. In addition, forgetting a password is a common mistake of most users.
The chances of you forgetting your own biometrics? Biometric authentication requires its input is present upon authorization. Biometrics like face patterns, fingerprints, iris scanning, and others are near-impossible to replicate with current technology. There's a one in 64 billion chance that your fingerprint will match up exactly with someone else's[1].
As the world increases its use of biometric authentication systems like facial recognition technology and other biometric security measures, privacy of users needs to be taken into consideration. When biometrics are converted into data and stored, particularly in places or countries that have large surveillance measures, a user runs the risk of leaving a permanent digital record that can be potentially tracked by nefarious actors.
In many instances, organizations and governments have used facial recognition software to track and identify people with scary accuracy that significantly inhibits privacy[3].
As surveillance increases, biometric data can become a permanent digital tag that can be used to track someone, both with and without their knowledge. Minimizing demographic bias in biometrics while verifying applicants' identities during digital onboarding is a challenge for providers.
Poor implementation of technology or deliberate misuse can result in discrimination and exclusion. Without a proven, document-centric identity proofing solution, cross-demographic performance can be unreliable and limit customer access to essentials like credit and the expanding range of digital services.
For example, a mobile biometric device will scan an entire fingerprint during the enrollment phase, and convert it into data. Download a new executive brief on biometrics, fairness, and inclusion by Steve Ritter, CTO at Mitek.
Mir scheint es die bemerkenswerte Phrase